Argo CD is a widely used delivery tool for Kubernetes. It uses declarative, GitOps-style workflow management. DevOps managers can safely deploy apps into production using progressive delivery such as canary and blue-green. Argo CD is Kubernetes-native and works with almost all source code management tools like Git, ButBucket, etc. But since it is open-source, the SecOps team in your organization will have security checks to be ticked before Argo CD can be used for production deployments.
“How to setup LDAP server in ArgoCD”
Argo supports many security protocols for authentication and authorization: SAML, OAuth, OIDC, LDAP, and SSO. If interested, please read how to enable SSO in Argo CD using Okta.
“What is the difference between LDAP and OpenLDAP?”
OpenLDAP is a free, open-source implementation of the LDAP protocol. Because it’s a common, free iteration available to anyone, OpenLDAP is sometimes referred to as just “LDAP.” However, it is more than just the protocol; it’s light LDAP directory software.
This blog will discuss how to configure LDAP and OpenLDAP for Argo CD. Although there are many ways to configure LDAP, I have considered Helm Charts. We will be using Dex to delegate authentication to an external identity provider.
Steps to configure LDAP in Argo CD
1. “Install” ArgoCD from this Git repo:
2. Install ingress
# kubect create ns ingress-nginx
# helm repo add ingress-nginx https://kubernetes.github.io/ingress-nginx
# helm install ingress-nginx ingress-nginx/ingress-nginx -n ingress-nginx
3. Install cert-manager
# kubectl create namespace cert-manager
# helm repo add jetstack https://charts.jetstack.io
# helm install cert-manager jetstack/cert-manager --set installCRDs=true -n cert-manager
4. Create cluster issuer
apiVersion: cert-manager.io/v1
kind: ClusterIssuer
metadata:
name: letsencrypt
spec:
acme:
server: https://acme-v02.api.letsencrypt.org/directory
email: mahesh.kota@opsmx.io
privateKeySecretRef:
name: letsencrypt
solvers:
- http01:
ingress:
class: nginx
5. Create ingress
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
annotations:
cert-manager.io/cluster-issuer: letsencrypt
kubernetes.io/ingress.class: nginx
nginx.ingress.kubernetes.io/backend-protocol: HTTPS
nginx.ingress.kubernetes.io/force-ssl-redirect: "true"
nginx.ingress.kubernetes.io/ssl-passthrough: "true"
name: argocd-ingress
namespace: argocd
spec:
rules:
- host: argocd.argo.opsmx.net
http:
paths:
- backend:
service:
name: argocd-server
port:
name: https
path: /
pathType: ImplementationSpecific
tls:
- hosts:
- argocd.argo.opsmx.net
secretName: argocd-tls-certificate
6. Configure LDAP
7. Create a file patch-dex.yaml file
NOTE : make sure you have the server URL
Here it is using LDAP
apiVersion: v1
data:
url: https://argocd.argo.opsmx.net
dex.config: |
connectors:
- type: ldap
name: ldap.opsmx
id: ldap
config:
# Ldap server address
host: "ldap.opsmx.com:389"
insecureNoSSL: true
insecureSkipVerify: true
# Variable name stores ldap bindDN in argocd-secret
bindDN: "$dex.ldap.bindDN"
# Variable name stores ldap bind password in argocd-secret
bindPW: "$dex.ldap.bindPW"
usernamePrompt: Username
# Ldap user search attributes
userSearch:
baseDN: "ou=users,dc=opsmx,dc=com"
filter: ""
username: uid
idAttr: uid
emailAttr: mail
nameAttr: displayName
# Ldap group search attributes
groupSearch:
baseDN: "ou=groups,dc=opsmx,dc=com"
filter: "(objectClass=groupOfNames)"
userAttr: DN
groupAttr: member
nameAttr: cn
8. Patch the Configmap
kubectl -n argocd patch configmaps argocd-cm --patch "$(cat patch-dex.yaml)"
9. Once it is patched CM argocd-cm looks like below
10. Disable admin if required admin.enabled: “false“
apiVersion: v1
data:
admin.enabled: "false"
application.instanceLabelKey: argocd.argoproj.io/instance
dex.config: |-
logger:
level: debug
connectors:
- type: ldap
name: ldap.opsmx
id: ldap
config:
# Ldap server address
host: "ldap.opsmx.com:389"
insecureNoSSL: true
insecureSkipVerify: true
# Variable name stores ldap bindDN in argocd-secret
bindDN: "$dex.ldap.bindDN"
# Variable name stores ldap bind password in argocd-secret
bindPW: "$dex.ldap.bindPW"
usernamePrompt: Username
# Ldap user serch attributes
userSearch:
baseDN: "ou=users,dc=opsmx,dc=com"
filter: ""
username: uid
idAttr: uid
emailAttr: mail
nameAttr: displayName
# Ldap group serch attributes
groupSearch:
baseDN: "ou=groups,dc=opsmx,dc=com"
filter: "(objectClass=groupOfNames)"
userAttr: DN
groupAttr: member
nameAttr: cn
exec.enabled: "false"
server.rbac.log.enforce.enable: "false"
url: https://argocd.argo.opsmx.net
kind: ConfigMap
metadata:
name: argocd-cm
namespace: argocd
NOTE: Variables dex.ldap.bindDN and dex.ldap.bindPW are defined in argocd-secret.
11. Patch the secret
kubectl -n argocd patch secrets argocd-secret --patch "{\"data\":{\"dex.ldap.bindPW\":\"$(echo XXPASWDXXXXX | base64 -w 0)\"}}"
Note:- please provide the password
12. Patch the secret
kubectl -n argocd patch secrets argocd-secret --patch "{\"data\":{\"dex.ldap.bindDN\":\"$(echo cn=XXXXXX,dc=opsmx,dc=com | base64 -w 0)\"}}"
13. Once patched the configmap and secret RESTART the dex-server and argocd-server
kubectl delete po -l app.kubernetes.io/component=server -n argocd
kubectl delete po -l app.kubernetes.io/component=dex-server -n argocd
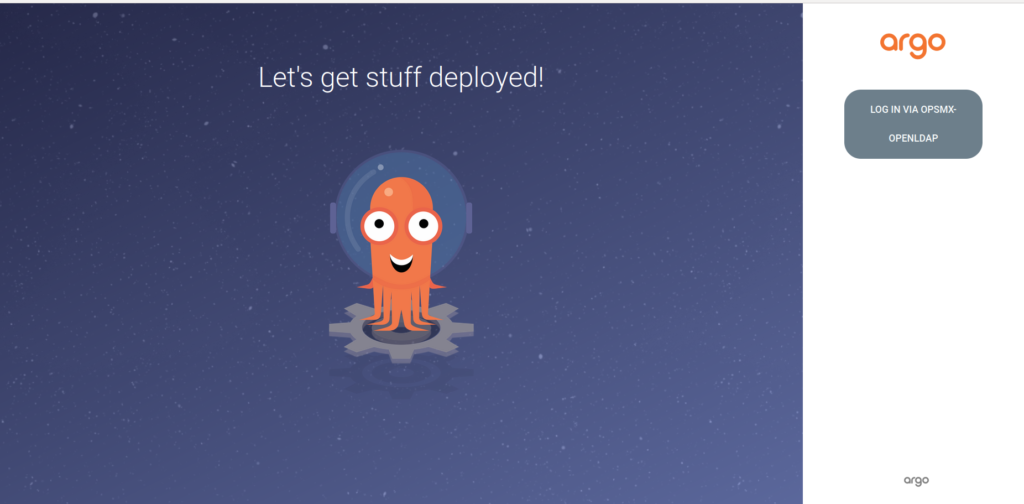
14. Access the UI with the URL, UI looks as below, CLICK on LOG IN LDAP.OPSMX
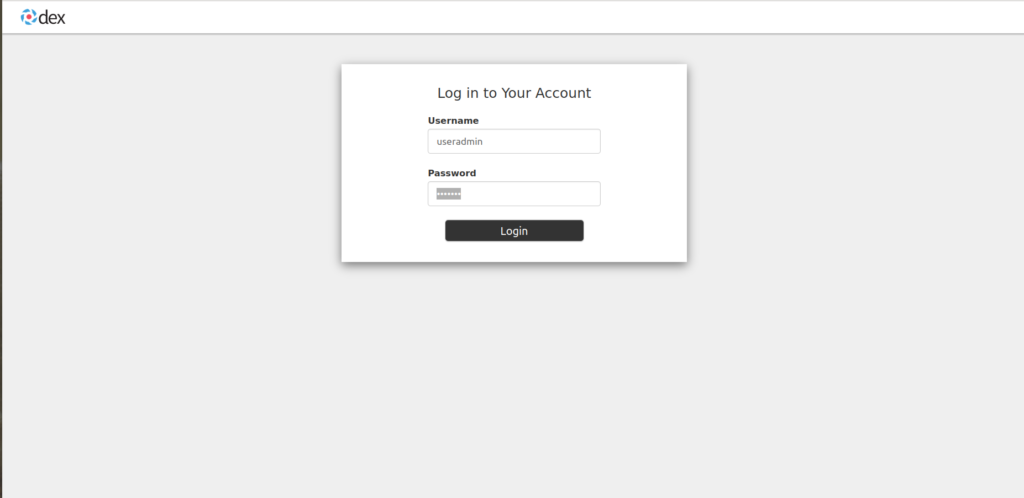
15. Provide your LDAP credentials
16. Once the user logged in you can find the groups in the dex-server
kubectl logs -f argocd-dex-server-578545c8f7-27mn4 -n argocd
time="2022-08-05T15:15:52Z" level=info msg="dex config unmodified"
time="2022-08-05T15:17:07Z" level=info msg="performing ldap search ou=users,dc=opsmx,dc=com sub (uid=mahesh.kota@opsmx.io)"
time="2022-08-05T15:17:07Z" level=info msg="username \"mahesh.kota@opsmx.io\" mapped to entry uid=mahesh.kota@opsmx.io,ou=users,dc=opsmx,dc=com"
time="2022-08-05T15:17:07Z" level=info msg="performing ldap search ou=groups,dc=opsmx,dc=com sub (&(objectClass=groupOfNames)(member=uid=mahesh.kota@opsmx.io,ou=users,dc=opsmx,dc=com))"
time="2022-08-05T15:17:07Z" level=info msg="login successful: connector \"ldap\", username=\"mahesh\", preferred_username=\"\", email=\"mahesh.kota@opsmx.io\", groups=[\"rxgroup\" \"rogroup\" \"spin-rxgroup\" \"jenkins-rxgroup\"]"
17. Define groups in the cm argocd-rbac-cm RBAC Resources and Actions
apiVersion: v1
data:
policy.csv: |
p, role:none, *, *, */*, deny
g, rxgroup, role:admin
g, adminchange, role:admin
policy.default: role:none
scopes: '[groups, uid]'
kind: ConfigMap
metadata:
name: argocd-rbac-cm
namespace: argocd
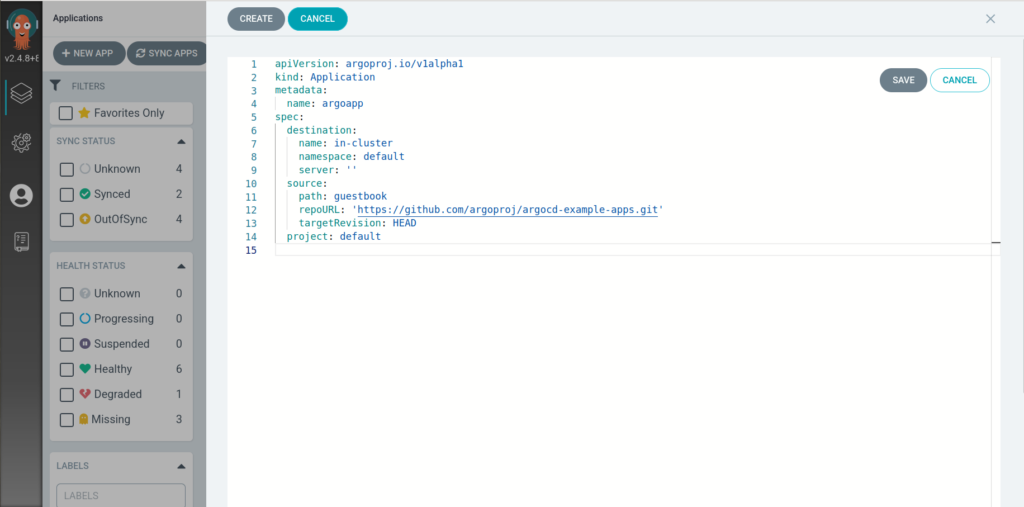
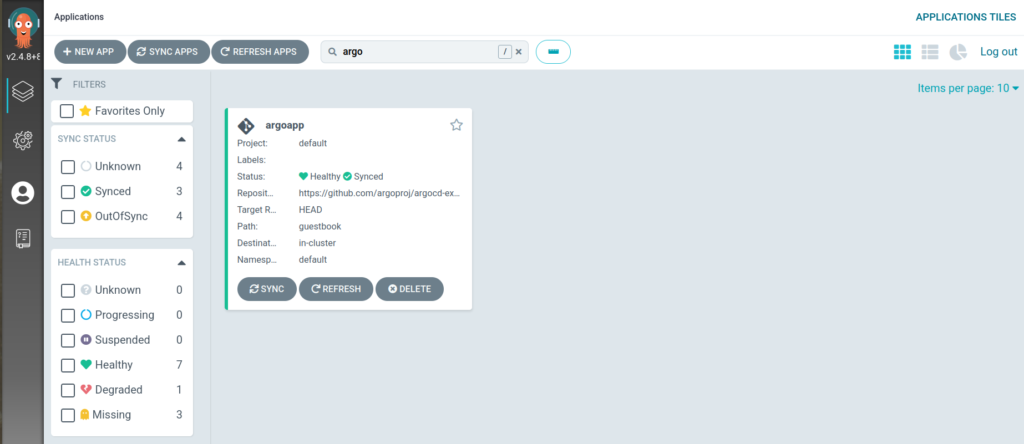
18. Now try to create application with default project(default) and cluster(in-cluster)
19. Create app can be either from UI or YAML edit in UI
20. Here it is YAML
apiVersion: argoproj.io/v1alpha1
kind: Application
metadata:
name: argoapp
spec:
destination:
name: in-cluster
namespace: default
server: ''
source:
path: guestbook
repoURL: 'https://github.com/argoproj/argocd-example-apps.git'
targetRevision: HEAD
project: default
21. SAVE it and SYNC it
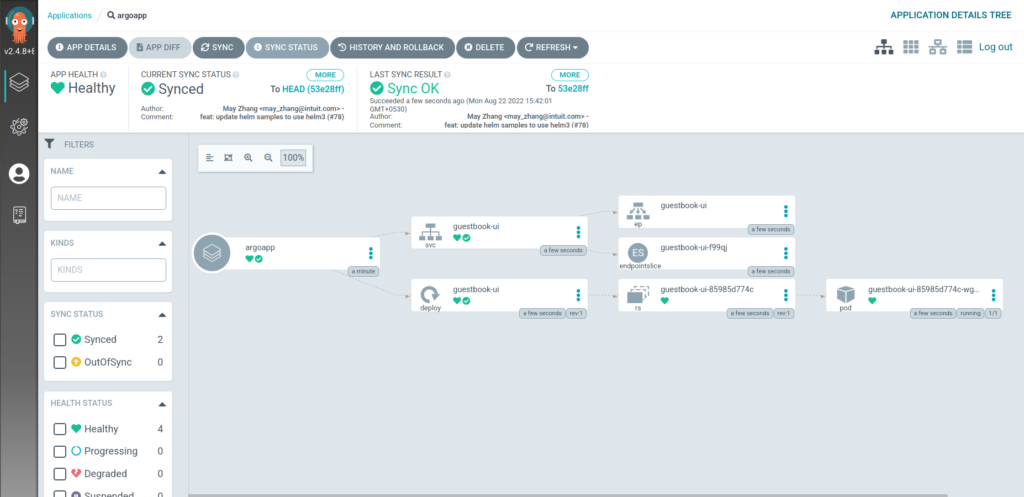
22. Click on Application you can see deployments
OpsMx Secure CD (powered by Argo CD) is the industry’s first Software Delivery and Deployment solution specifically designed for Enterprise Security and Compliance.
- Manage security posture
- Accelerate multicloud and Kubernetes deployments
- Automate approvals
- Block vulnerabilities
- Enforce policy compliance

Steps to configure OpenLDAP in Argo CD
1. Make sure openLDAP is installed in your package and check the service
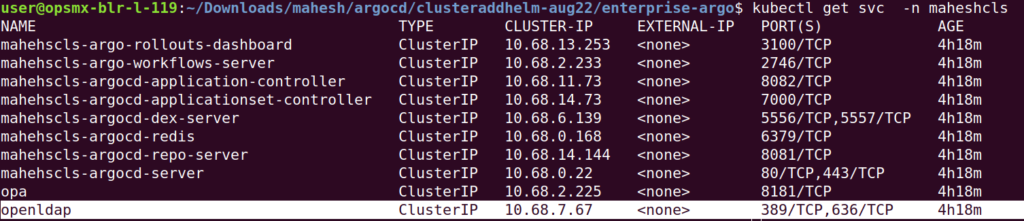
2. Edit the configmap argocd-cm and below configuration for openldap
Note: disable admin if not required admin.enabled: “false”
Variables dex.ldap.bindDN and dex.ldap.bindPW are defined in argocd-secret.
apiVersion: v1
data:
admin.enabled: "false"
application.instanceLabelKey: argocd.argoproj.io/instance
dex.config: |-
connectors:
- type: ldap
name: opsmx-openldap
id: ldap
config:
# Ldap server address
host: "mahesh-openldap:389"
insecureNoSSL: true
insecureSkipVerify: true
# Variable name stores ldap bindDN in argocd-secret
bindDN: "$dex.ldap.bindDN"
# Variable name stores ldap bind password in argocd-secret
bindPW: "$dex.ldap.bindPW"
usernamePrompt: Username
# Ldap user serch attributes
userSearch:
baseDN: "dc=example,dc=org"
filter: "(objectClass=simpleSecurityObject)"
username: cn
idAttr: cn
emailAttr: cn
nameAttr: cn
# Ldap group serch attributes
groupSearch:
baseDN: "dc=example,dc=org"
filter: "(objectClass=simpleSecurityObject)"
userAttr: cn
groupAttr: cn
nameAttr: cn
exec.enabled: "false"
server.rbac.log.enforce.enable: "false"
url: https://argocd-test.ninja-test.opsmx.net
kind: ConfigMap
metadata:
name: argocd-cm
namespace: mahesh
3. Patch the secret for Variables dex.ldap.bindDN and dex.ldap.bindPW
kubectl -n mahesh patch secrets argocd-secret --patch "{\"data\":{\"dex.ldap.bindPW\":\"$(echo xxxxxxxxx | base64 -w 0)\"}}"
kubectl -n mahesh patch secrets argocd-secret --patch "{\"data\":{\"dex.ldap.bindDN\":\"$(echo cn=admin,dc=example,dc=org | base64 -w 0)\"}}"
4. Once patched the configmap and secret RESTART the dex-server and argocd-server
kubectl delete po -l app.kubernetes.io/component=server -n argocd
kubectl delete po -l app.kubernetes.io/component=dex-server -n argocd
5. Access the UI with the URL, UI looks as below, CLICK on LOG IN LDAP.OPSMX
If you identify we dont see default login by disabling the admin.enabled: “false” in argocd-cm configmap
7. Click on the LOGIN VIA OPENLDAP and provide admin/opsmxadmin123
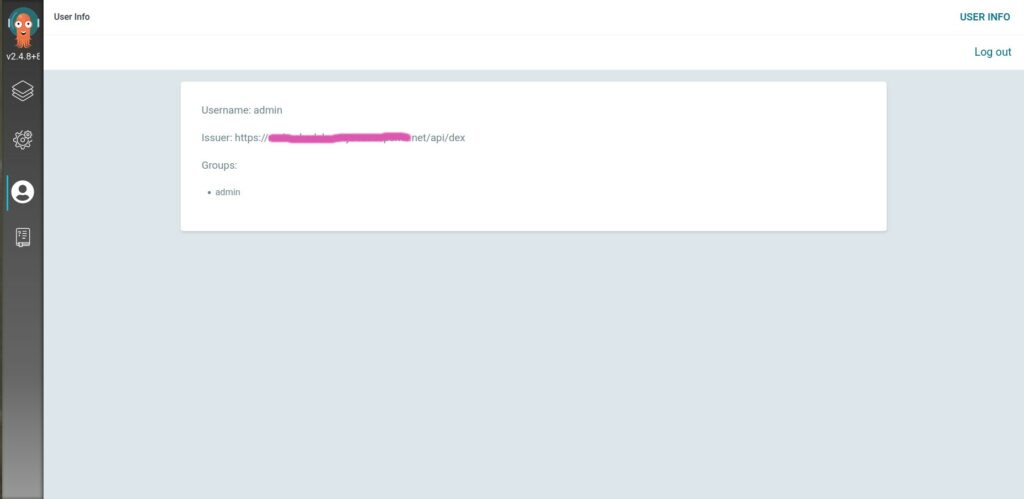
7. Finally it login successfully and you can see the info in the User
8. Logs of the dex-server pod can be like this
kubectl logs -f -l app.kubernetes.io/component=dex-server -n mahesh
ime="2022-08-09T06:49:52Z" level=error msg="ldap: invalid password for user \"cn=admin,dc=example,dc=org\""
time="2022-08-09T06:49:58Z" level=info msg="performing ldap search dc=example,dc=org sub (&(objectClass=simpleSecurityObject)(cn=admin))"
time="2022-08-09T06:49:58Z" level=info msg="username \"admin\" mapped to entry cn=admin,dc=example,dc=org"
time="2022-08-09T06:49:58Z" level=info msg="performing ldap search dc=example,dc=org sub (&(objectClass=simpleSecurityObject)(cn=admin))"
time="2022-08-09T06:49:58Z" level=info msg="login successful: connector \"ldap\", username=\"admin\", preferred_username=\"\", email=\"admin\", groups=[\"admin\"]"
Conclusion
Argo CD is a graduate from CNCF and is the most popular GitOps tool, however setting enterprise security measures and policies can be a hassle. To help you unlock the power of GitOps from Day 1, OpsMx provides Intelligent Software Delivery (ISD) for Argo, which comes with all the bells and whistles for security and scale requirements for your software delivery. Try ISD for Argo for free.
OpsMx also provides Argo Center of Excellence (COE) for enterprises needing expert services or consultation on Argo CD and Argo Rollout implementation to expedite their GitOps journey.
About OpsMx
Founded with the vision of “delivering software without human intervention,” OpsMx enables customers to transform and automate their software delivery processes. OpsMx builds on open-source Spinnaker and Argo with services and software that helps DevOps teams SHIP BETTER SOFTWARE FASTER.





0 Comments