Table of Contents
What is “Zero Trust security” model?
In simple terms, Zero Trust security is a cybersecurity model based on the principle of “never trust, always verify“. This model enables DevSecOps teams to better handle vulnerabilities in the wake of increasing cyber threats.
In a Zero Trust architecture, access to resources is not implicitly trusted, regardless of whether the access request is coming from inside or outside the network perimeter. Instead, every access attempt is carefully authenticated, authorized, and continuously validated, regardless of the user’s location or device.
What is the need to embrace Zero Trust security?
The idea of trusting anyone inside the organization’s network is a massive flaw that needed rethinking. The ‘security’ wing in tech organizations did not level up with the pace of digital transformations like cloud migration, decentralized infrastructure, and container technologies.
Though these have enabled engineering teams to deliver products and services faster, the traditional security practices still left massive gaps for attackers to exploit. While Zero Trust has become a standard in recent years, as of today it has been formalized as a response to securing digital transformation in the wake of increasing cyber attacks.
What is the architecture of Zero Trust security?
The core ideology of a Zero Trust security architecture is to trust no one and always verify and validate every digital interaction. This approach minimizes the risk of security breaches by assuming that threats may already exist within the network and ensuring that access is granted on a need-to-know basis, with the least privilege necessary to perform the required tasks.
This strategy also helps security teams to organize and strategize accordingly to counter threats. In the context of a CICD pipeline, Zero Trust is all about integrating security into the DNA of the DevOps framework.
Let us understand some key tenets that can help the DevSecOps and Security team to implement Zero Trust Security initiatives into their ecosystem.
Why is Zero Trust Necessary for Your Continuous Delivery Pipeline?
A Zero Trust ecosystem is difficult to achieve from a technical and cultural aspect, but when done right, the effects can be far-reaching. Of course, it will also be a time-consuming and resource-intensive process. It’s imperative that DevSecOps add this security dimension while developing the software instead of the last priority. Let us discuss some reasons why Zero Trust has become so important to DevOps.
1. Perimeter security is obsolete.
Traditionally, IT organizations assumed anything inside their network as secure. Unfortunately, that is not the case anymore. Security is more important now than ever. Inadequate perimeter-based security strategies that worked for the container environment are an invitation to disaster today. The systems that are geared to deflect external attacks have become increasingly vulnerable from the inside, too. Advanced trojan files and malicious software can easily breach perimeter-based defense security to cripple the entire IT ecosystem.
2. Cloud is less secure.
Today, organizations have distributed multi-cloud applications and services that are accessible from anywhere in the world and on any device. So, when an organization deploys its application on a public cloud such as Google Amazon or Azure, the data travels/spreads outside the safety of their on-premises servers.
Solar winds mega-breach and Colonial Pipeline’s DarkSide Intrusion are two major security incidents where entire infrastructure got compromised by malware attacks.
3 Implementing security best practices is as important as coding.
While microservices and distributed architecture do enable agility and scalability, they also bring in additional responsibilities for the developers and engineers. Besides writing business logic and codes, now they also have to tackle security and networks as well.
4. Remote is the new normal.
Most modern IT organizations have adopted remote-first or hybrid work arrangements which entails that their workforce will be global and distributed. As a result, increasingly customers and employees access the IT network from unsecured IPs through unmanaged devices. This makes it difficult for IT teams to ensure the security of the network against a growing sophistication of attackers. Moreover, the home network of employees poses more vulnerability, putting the business at risk.
5. Patchwork leads to vulnerabilities.
Organizations implementing patchwork security practices become more susceptible to threats, which is why their security teams are more likely to spend more time managing these devices.
6. Lack of Security-first initiatives.
The increasing adoption of Software Delivery Orchestration tools has empowered teams to speed up deployments. Now, organizations can deploy applications into production on-demand. However, organizations are still lagging in adopting a security mindset with a systematic approach and infrastructure.
What Are the Top Three Core Zero Trust Principles?
Zero Trust aims at securing your data, applications, and network by providing an identity-centric policy model for controlling access. By adhering to these three guiding principles, DevSecOps teams can establish a zero trust foundation.
1. Ensuring all resources are connected and accessed securely, regardless of location.
In a Zero Trust ecosystem, DevSecOps teams must ditch the castle-and-moat model of security and open the applications’ access to the world wide web, securely. By doing so, they remove the barriers that have existed between security tools and teams.
This principle also mandates that all humans and machines must have secured access to business resources, such as data applications and servers. This access must be provided regardless of the location of identity, location of data, or technology of the resource being accessed. In short, teams must design systems that will encrypt network traffic and mandate access only through an authentication policy model.
2. Adopting a least privilege strategy and strictly enforcing access control.
The least privilege strategy has been around for many years, but it wasn’t always easy to enforce due to the complexities involved. Before the DevSecOps culture, teams associated with software delivery managed privileges collectively where anyone within the group would have uniform access. But Zero Trust adopts compliance-based access where privileges are not limited to a particular group but to a role, they have to play. Therefore, DevSecOps teams must frame compliance policies that will consistently manage user access across locations and resource types, and at both the network and application layer.
The existing security solutions are not adequate, as they can either cater to a network or an application layer. This allows users to gain broad access to a network with their own devices but relies on applications for authentication. For example, anyone can log in to a banking website, but only a user with banking access can access the application. This security flaw lets attackers use DDOS to stall servers and services.
However, according to Zero Trust principle, if users are not authorized to access a particular service (e.g., having credentials to SSH into a server, or to authenticate to a VPN), they must not have the ability to connect to that service at a network layer.
3. Inspecting and logging all events.
Networks allow distributed IT components to connect with one another. This is the sole reason why zero trust mandates inspecting and logging network traffic. And while it is important that the zero trust system broadly examines and logs network traffic metadata, it must do this judiciously as it can cost a fortune to process and store it.
Plus, the zero trust system should enrich network traffic content by adding identity and context before feeding it into the monitoring tools. This will enhance their ability to detect and alert incidents, thus improving response.
What are the Extended Zero Trust Principles?
DevSecOps team must take security a notch further to achieve an enterprise-class Zero Trust environment.
1. Ensuring all components support APIs for event and data exchange.
With disparate systems, DevSecOps teams must standardize all communications for extensibility. A Zero Trust system should enforce a holistic security policy where nothing will be a silo anymore. As stated by the first policy of the core principle, all components of the ecosystem must be able to integrate with one another.
These integrations will not only help in exchanging data and information but also initiate a response to security events. (3rd core principle). Every siloed component adds friction, thus diminishing the effectiveness of a Zero Trust system. On the other hand, every IT component integrated with the ecosystem adds value.
2. Automating actions across environments and systems, driven by context and events.
Automation is crucial for a Zero Trust environment of any scale. Zero Trust relies on dynamic access control rules which change depending on identity, device, network, and context. Whether enforcing new policies across the ecosystem or implementing dynamic policies to ensure that external and internal entities remain trustworthy, automation is necessary for all these scenarios.
That said, automation doesn’t just mean “automatic”. In reality, most workflows will need a manager or security expert to approve the workflows after reading and verifying the necessary checks.
3. Delivering tactical and strategic value.
A Zero Trust project has a significant impact on infrastructure, teams, operations, and end-user experience. Though outcomes are positive, the DevSecOps team must ensure that they provide business value.
Benefits of Adopting a Zero Trust Architecture
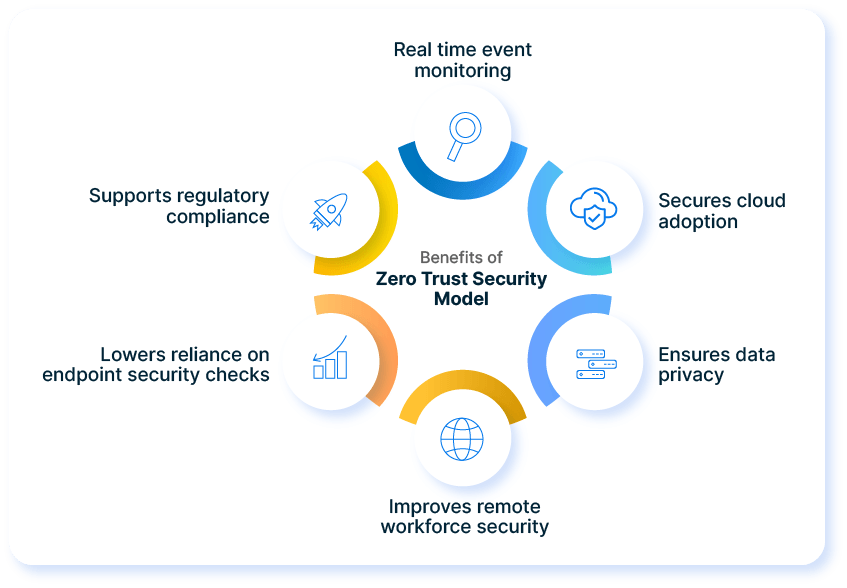
- Monitors events in real-time and aids corrective actions: Data logging and monitoring ensure that abnormal and fraudulent activities and access are instant detected and security automation ensures that such events gets isolated instantly.
- Secures cloud adoption: Cloud adoption has its reservations because organizations lose visibility and access. However, a zero trust architecture ensures access is enforced based on strict policies. It is also advised to closely monitor logs to maintain the health of the system.
- Ensures data privacy: The personal data of the customers stay secure with strong authentication and validations protocols.
- Improves remote workforce security: As an increasing number of businesses become remote-first and remote-friendly, zero trust architecture ensures all communications on the internet are secured, even from a remote location.
- Lowers reliance on endpoint protection: A least privilege strategy prevents or restricts endpoint hacking incidents, thus lowering collateral damage by restricting access.
- Supports regulatory compliance: A zero trust architecture can ease the journey to achieve new regulatory compliance certificates like General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), HIPAA, and a host of other regulatory compliance regulations.
OpsMx expedites zero trust principle adoption for your CI/CD Pipeline
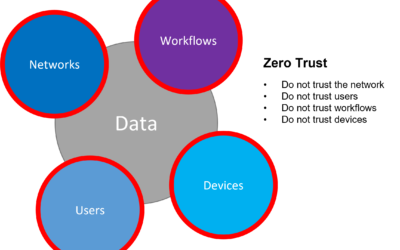
While adopting the Zero trust guiding principles, OpsMx emphasizes building robust pipelines that don’t trust any person, workflow, infra, or network.
So, now let us delve deeper to understand how OpsMx ISD can aid DevSecOps teams to meet the primary criteria of zero trust security.
Secured connection: Restrict Access using OAuth, SAML, LDAP, X.509, Github teams.
The OpsMx ISD can restrict access to pipelines, projects, and accounts by hooking into your current authentication systems, such as OAuth, SAML, LDAP, X.509 certs, Google groups, Azure groups, or GitHub teams.
Least privilege strategy: No one has the keys to the kingdom.
Keep Spinnaker configuration files in source control while protecting secrets with a 3rd party secret store- HashiCorp Vault, AWS KMS/ Key Store, or Azure Key Vault.
The Dynamic policy feature enables managers to simplify compliance requirements, both ongoing and upcoming. Thus, with ISD, DevSecOps teams gain the freedom and flexibility to tie policy and control into the rapidly changing IT services.
Smart Continuous event monitoring: Make automated and informed decisions
The OpsMx ISD platform offers instant visibility with correlated app visibility, which aids managers in making better decisions regarding app deployment. Additionally, they get access to rich insights and visibility into hidden data patterns, Metrics, API Data, and Transaction Traces.
Visit the Secure Software Delivery page to learn more!


0 Comments