The way we develop, deliver and operate software has changed
The evolution in how we develop, deliver, and operate software has led to an increase in the speed and scale of software changes we see daily in many enterprises. Yet, these changes are also introducing new security risks and expanding the attack surface of your software supply chain.
Change in Software Development: The use of Open Source and third-party components has increased significantly in our software development process. Today, open-source components constitute more than 70% of the code in an average application. According to a 2020 Synopsys survey, open-source components comprise an average of 75% of a typical application’s code. The adoption of open-source software provides benefits like faster time-to-market but also introduces security risks due to potential vulnerabilities in open-source components that attackers can exploit.
Change in Software Delivery: DevOps practices have further evolved the software delivery process by integrating development and operations teams, enabling more frequent and automated software releases. This involves using tools and processes to automate software build, test, and deployment, as well as implementing monitoring and feedback loops for continuous software quality improvement.
These changes have resulted in faster, more efficient software delivery, with teams capable of releasing software updates more frequently and responding quickly to changing market demands. However, this also brings new security challenges, as the increased speed of development and deployment can result in oversights in security testing and vulnerabilities in the software supply chain. Therefore, it is crucial for organizations to implement robust security controls throughout the software development and delivery process.
Change in Deployment and Operation of Software: The operation of software has changed dramatically in recent years due to the adoption of cloud computing and DevOps practices. Traditionally, software was installed and operated on-premises, with a dedicated IT team responsible for maintaining and updating the software. With cloud computing, the software is hosted and operated by a third-party provider.
These changes have resulted in more efficient, cost-effective software operations. Teams can easily deploy and manage software in the cloud, and respond quickly to changing market demands. However, this also introduces new security challenges, such as managing access to cloud-based systems and protecting against cloud-based attacks.
Attack surface is increasing and so are security attacks
Expanding Attack Surface of Your Supply Chain: As open-source and third-party components in software development proliferate, it broadens the potential attack surface. These attacks are increasingly innovative, targeting the most vulnerable parts of the supply chain for easier access and greater disruption potential. The interconnected nature of modern software ecosystems also means a single breach can have far-reaching implications. Therefore, the expanding attack surface demands a comprehensive approach to secure every stage of the software supply chain.
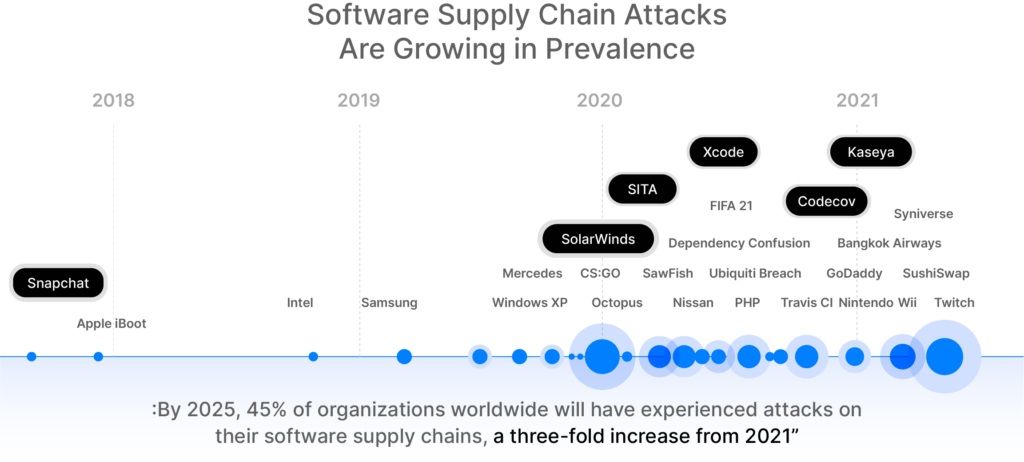
Rise in Security Attacks: The frequency of software supply chain attacks has seen a drastic rise in recent years. According to a report by Sonatype, supply chain attacks increased by 650% between 2019 and 2020.
The rate of software supply chain attacks may actually be higher than reported, as many attacks go undetected or unreported. As the use of third-party software components and faster releases due to DevOps continue to increase, it’s likely that supply chain attacks will remain a significant threat to organizations.
As software takes a central role in most organizations, mistakes can be catastrophic. Failing to protect the security of your delivery process becomes a liability for your company.
Re-thinking traditional solution approaches
To tackle these challenges, we need to rethink traditional approaches.
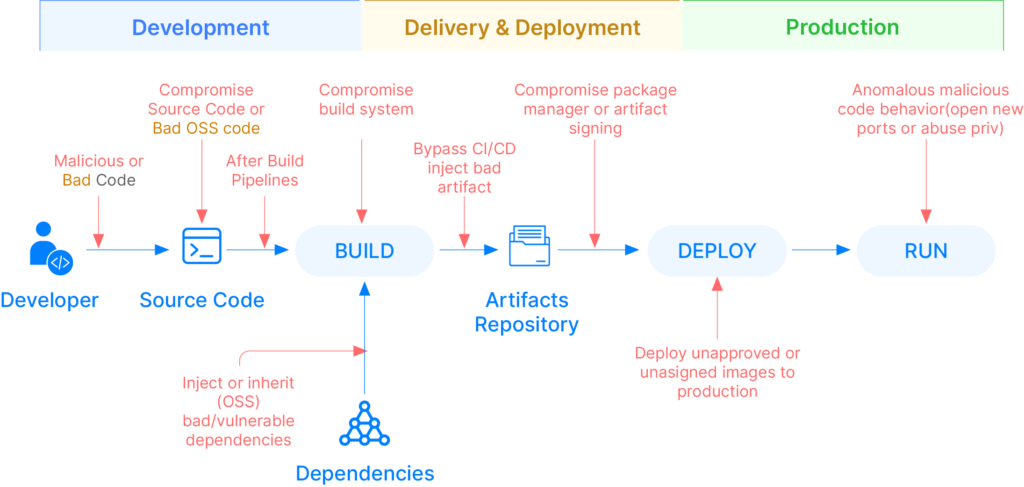
1. The traditional approach of focusing solely on attacks in production or attacks through code isn’t sufficient. We need to secure all stages of how we develop, deliver, and operate software. Security is only as strong as the weakest link.
During the delivery process, attacks can occur through processes, people, and tools. For example, a Fortune 100 CIO shared that he is concerned about the risk of a disgruntled DevOps or Ops Engineer compromising software without any trace of who did it. Some reasons why the delivery and deployment process increases security risks include:
- Tool Sprawl: The delivery process involves multiple tools and technologies, often used by different teams. This can lead to misconfiguration and increased complexity, creating security blind spots.
- Multiple Pipelines and Steps: The delivery process includes numerous stages, pipelines, and stakeholders, each of which expands the attack surface. Misconfigurations and skipped steps can occur when different teams interact with the same systems and infrastructure, leading to security vulnerabilities. Unvetted solutions by teams or individuals, known as Shadow IT, can further compound these risks.
- DevOps Prioritizes Efficiency: The primary focus of DevOps is rapid software delivery, which can sometimes sideline security considerations. While DevOps teams excel at making things work, they may lack the security expertise of dedicated security teams, resulting in overlooked or underestimated security risks.
- Third-Party Tools Risks: DevOps teams frequently rely on third-party software and services, which can introduce additional security risks. These risks include:
- Vulnerability Exploitation: Third-party components may harbor vulnerabilities that attackers can exploit to gain unauthorized access or data.
- Malware Distribution: Malware can be concealed within third-party libraries or packages, enabling attackers to infiltrate systems or steal sensitive data.
- Supply Chain Attacks: Attackers may compromise the supply chain of a third-party component, inserting malicious code to gain unauthorized access.
- Compliance Violations: Use of non-compliant third-party components can result in fines, legal liability, and reputational damage.
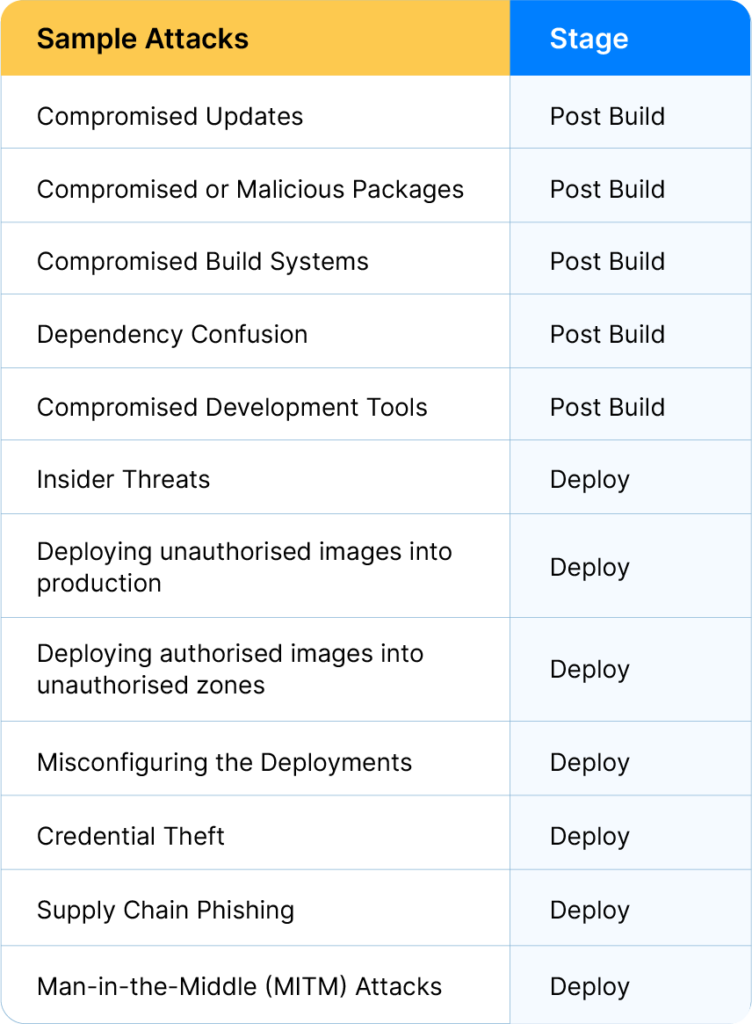
The graphic and table below illustrate possible attack types during the delivery and deployment. As the pace and scale of software changes accelerate, securing the delivery process becomes increasingly crucial.
2. Enterprises should not have to make a trade-off between security and delivery speed. It is critical to achieve both the goals of security and delivering diverse apps @ speed.
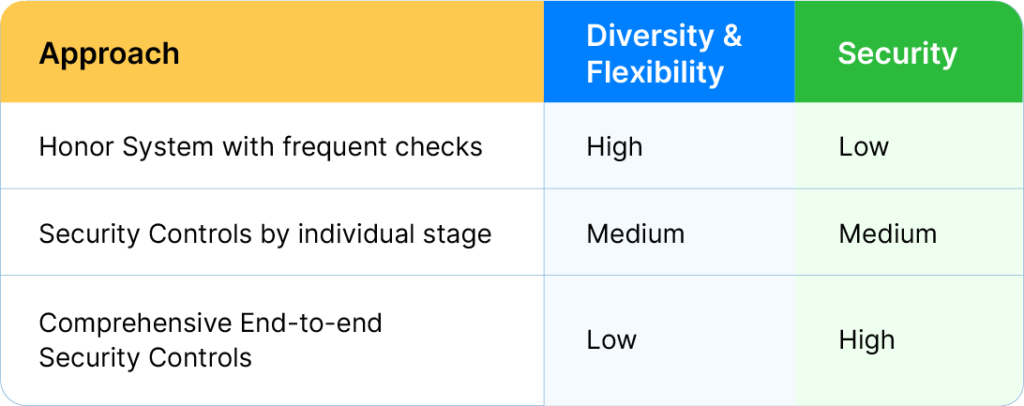
Most large enterprises have a diverse set of applications needing the flexibility in delivery. Today, security conscious enterprises use a range of approaches to balance between security and speed needs.
On one end of the spectrum, we have the “Honor system with frequent checks”, where a set of best practices are expected and the security teams perform checks that the best practices are followed. In the “Honor system”, as the scale increases, checks become harder to perform and attest.
On the other end of the spectrum, we have enterprises that implement comprehensive end-to-end controlled pipelines”. In this approach it is harder to on-board new services and causes friction to speed.
A data driven approach that can plug-into your devops process and tools promises to the benefits of both the speed and security.
Reinventing Delivery Security with Data-Driven Strategies
In the wake of the ‘Executive Order on Improving the Nation’s Cybersecurity‘ our customers have been working with us to enhance our Secure Software Delivery to secure their software delivery, audit and to attest their entire delivery process.
We have been working with a select customers of different sizes, a Fortune 10, several Fortune 500 and midsize enterprises and enhanced our SSD offering.
We understood that changing existing processes, tools and imposing new security expectations from developers and DevOps is hard to implement in large scale organisations. So we designed an approach this requires minimal changes and plugs-into an existing enterprise in the following way:
- Plugs into the customer’s delivery process – without needing to change their process
- Integrates with their delivery tools – without restricting the tools they use
- Continuously Verifies & Protects – without imposing new restrictions on the diversity/freedom that developers and DevOps teams need
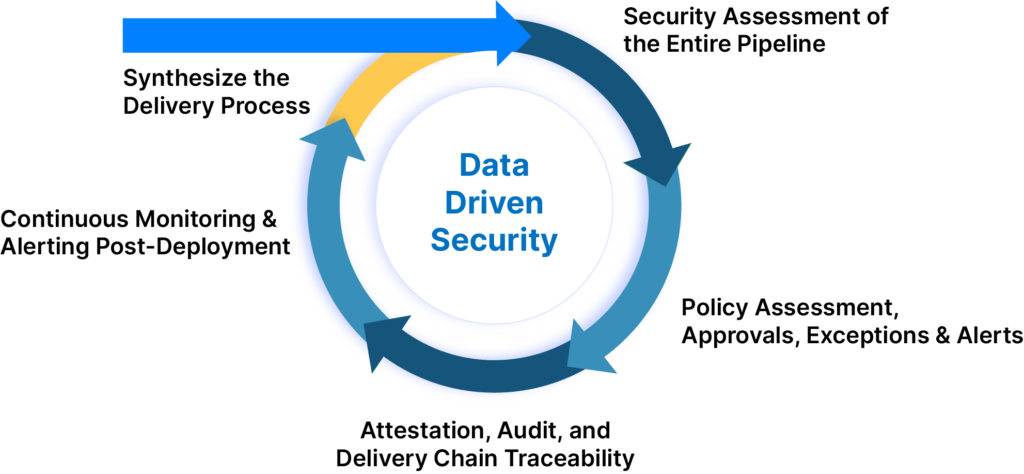
- Synthesis of the Delivery Process: With numerous pipelines running daily, gaining a holistic view of all the processes manually is not feasible. Automation is crucial in understanding the pipeline paths/processes.
- Automated Security Assessment: We provide an automated assessment framework that mitigates delays, errors, and human processing limits, enhancing security and productivity while reducing costs.
- Actions, Approvals, Exceptions, and Alerts: Automation is essential when handling thousands of pipelines daily and millions of deployments annually.
- Audit and Delivery Chain Traceability: Our solution offers the ability to audit, attest, and trace all critical steps in the software delivery process.
- Continuous Monitoring & Alerting Post Deployment: In an era of frequent new vulnerabilities, continuous monitoring of the security posture post-deployment is critical.
Conclusion
This blog post has aimed to shed light on the changing landscape of software delivery security. While the evolving digital environment continues to present new challenges, it’s clear that innovative, data-driven solutions can pave the way for secure, efficient, and flexible software delivery. By integrating security into every step of the delivery process, we can effectively mitigate risks without compromising on speed or diversity of applications. The future of software delivery lies in a paradigm where speed, security, diversity, and flexibility are not mutually exclusive but integral components of a robust delivery ecosystem. So it is imperative that teams of all sizes define best practices around delivery and deployment security.
About OpsMx
Founded with the vision of “delivering software without human intervention,” OpsMx enables customers to transform and automate their software delivery processes. OpsMx builds on open-source Spinnaker and Argo with services and software that helps DevOps teams SHIP BETTER SOFTWARE FASTER.



0 Comments