Delivery Firewall
A new way to enforce application security policies at the point of deployment, across staging & production environments
The OpsMx Delivery Firewall adds a gating mechanism to your existing CI/CD tools to guarantee compliance and prevent release of security vulnerabilities. Out of compliance release are automatically blocked before they get deployed
OpsMx is
Trusted By
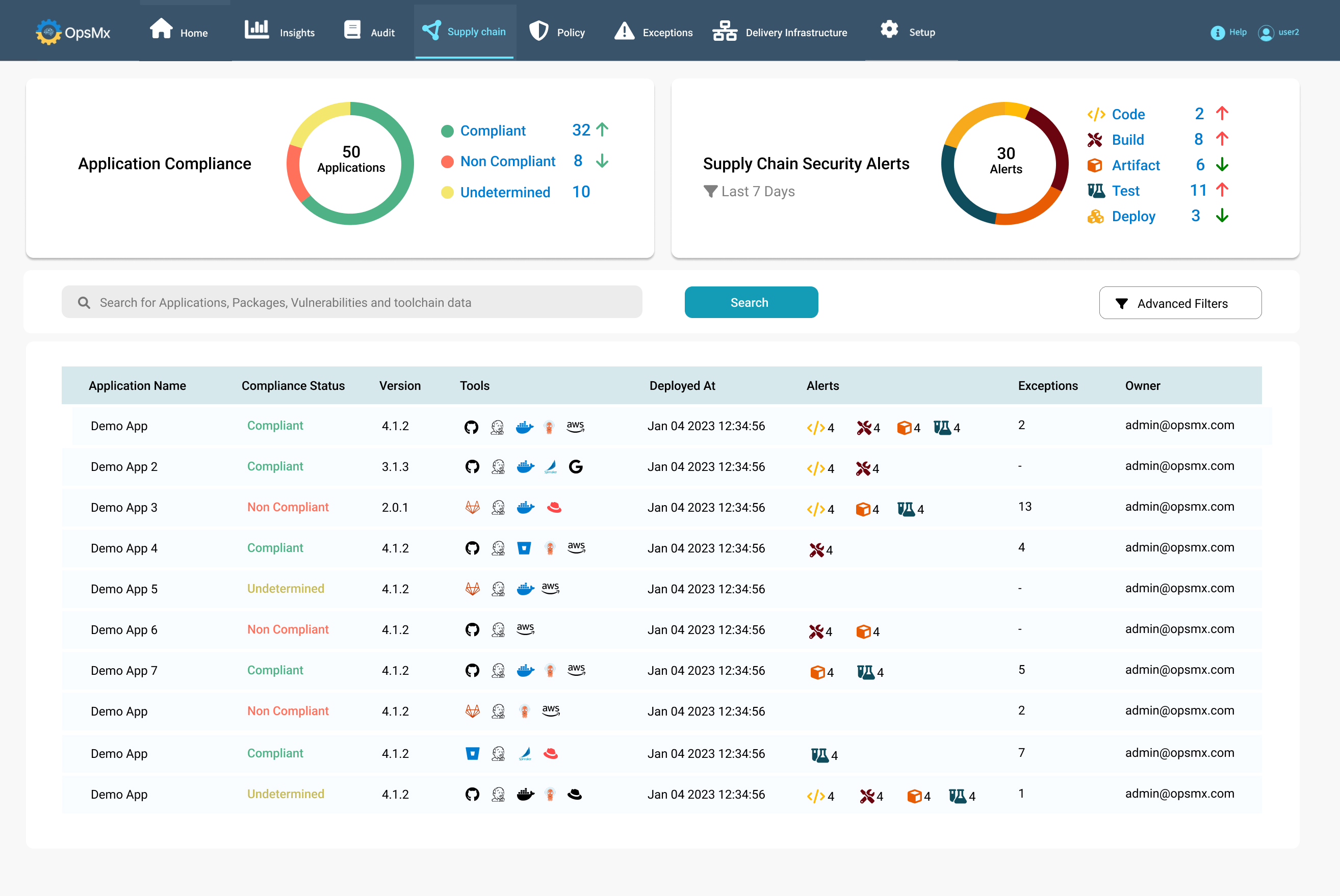
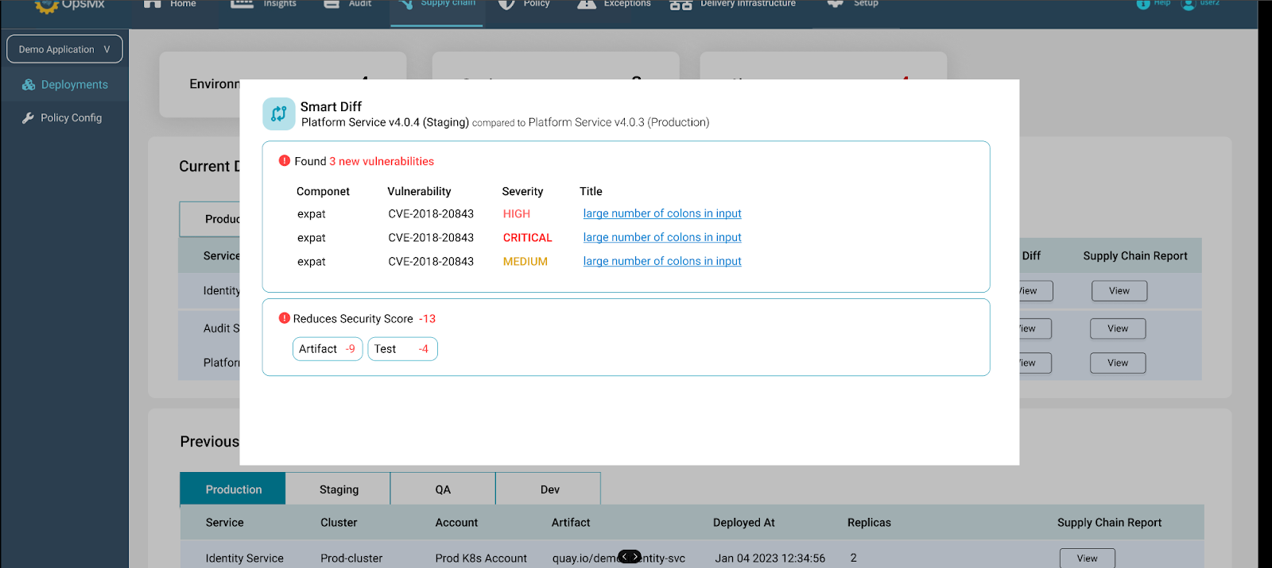
What is a Delivery Firewall?
The OpsMx Delivery Firewall is a new way to secure your application releases and enforce software supply chain security. Just like a network firewall enforces rules and policies that keep bad actors out of your network, a delivery firewall enforces your application security and DevSecOps policies to keep bad or insecure code from getting into production.
The delivery firewall works with leading CI/CD platforms, such as Jenkins, Argo, Spinnaker, GitLab and GitHub Actions. You specify the rules you want enforced for deployments, such as mandatory code scanning, no critical CVEs, approved change request ticket, or security review. The delivery firewall then runs in the background to automatically verify at the time of deployment that policies have been followed. The deployment of application releases that are out of compliance is blocked.
Key Capabilities
Deployment Security Enforcement
- Security policy checks for software deployments
- Policy enforcement engine to orchestrate and execute real-time policy checks before deployment
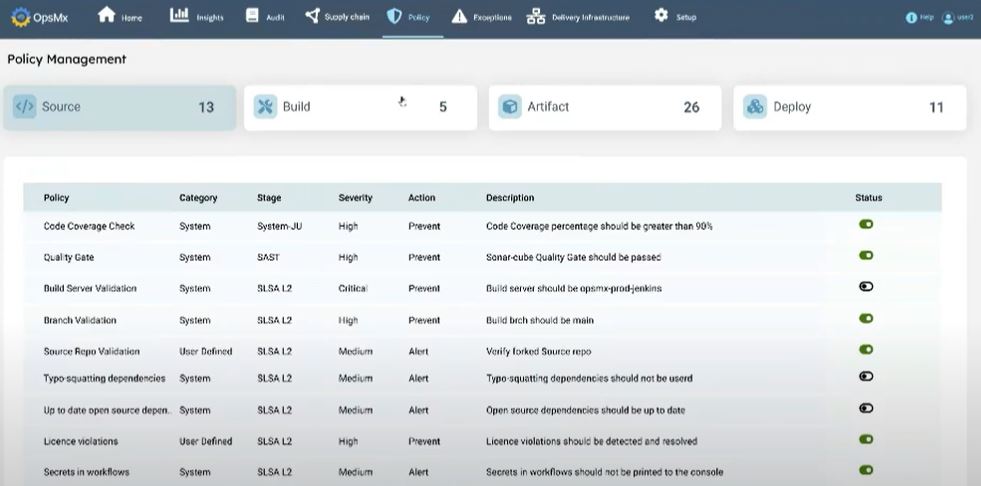
Policy Driven Automated Compliance
- Automate guard rails block release of insecure or out of compliance code
- Pre-packaged Deployment Policies / Security & Compliance Rules
- Support for regulatory compliances – to FedRamp, PCI, HIPAA, etc.
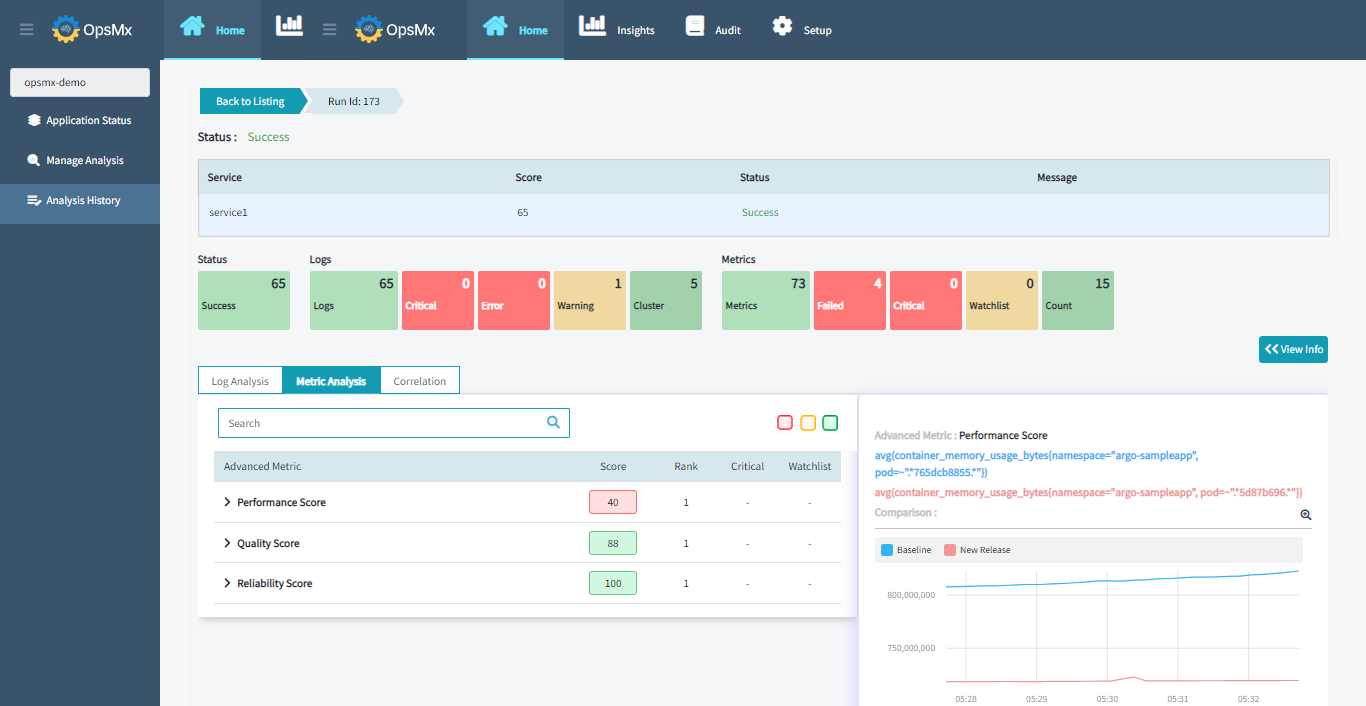
Automated Verification & Actionable Intelligence
- Automated risk scoring of releases analyzing data from security scan ecosystem
- Analyze open or broken firewall rules
- Automated data-driven decisions
Automated Approvals and Notifications
- Automated deployments / roll back based on deployment rules results
- Automate policy gates to ensure velocity
- Manage exceptions
- Notify and collaborate using existing channels (email, messaging, chat)
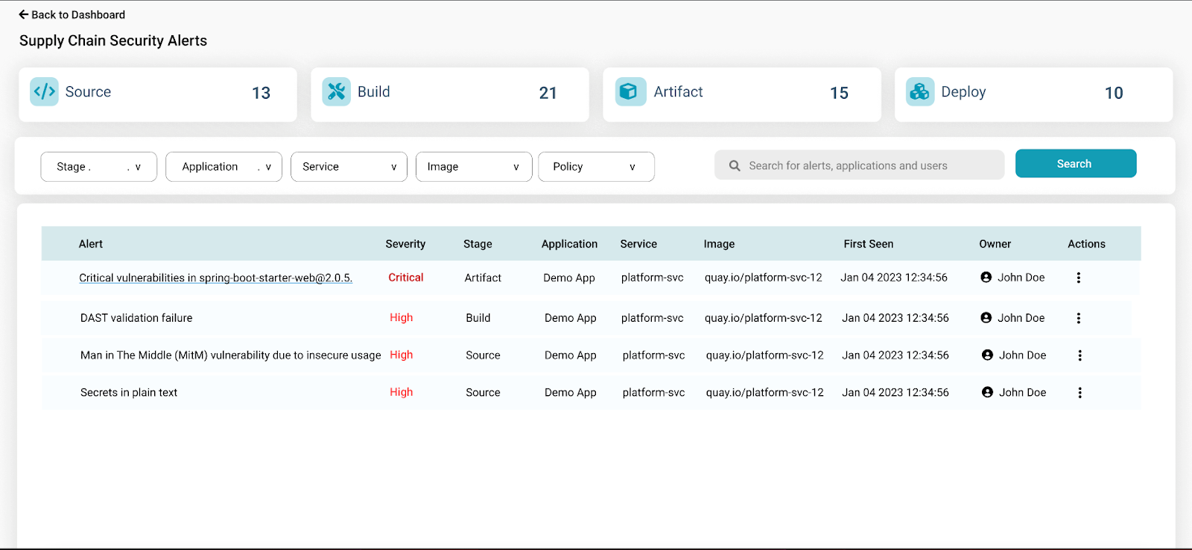
Automated Compliance and Audit
- Automated deployment security posture management against security data
- Deployment audit and attestation
- Compliance reports and dashboard
DevOps Toolchain Integrations
Secure Continuous Delivery Datasheet
Read about secure, automated, and scalable CD solution to reduce risk exposure and bring greater resilience and integrity to your applications
Top Reasons to Consider Deployment Security
Learn how radical changes in the delivery processes introduce new security risks and increase the attack surface.
Tackle the Threat of Software Supply Chain Attacks
Find the comprehensive solution to tackle real-time vulnerability risks and security breaches in your delivery process.