Delivery Bill of Materials (DeliveryBOM)
Track security, compliance, enforcement of your application delivery and deployment process
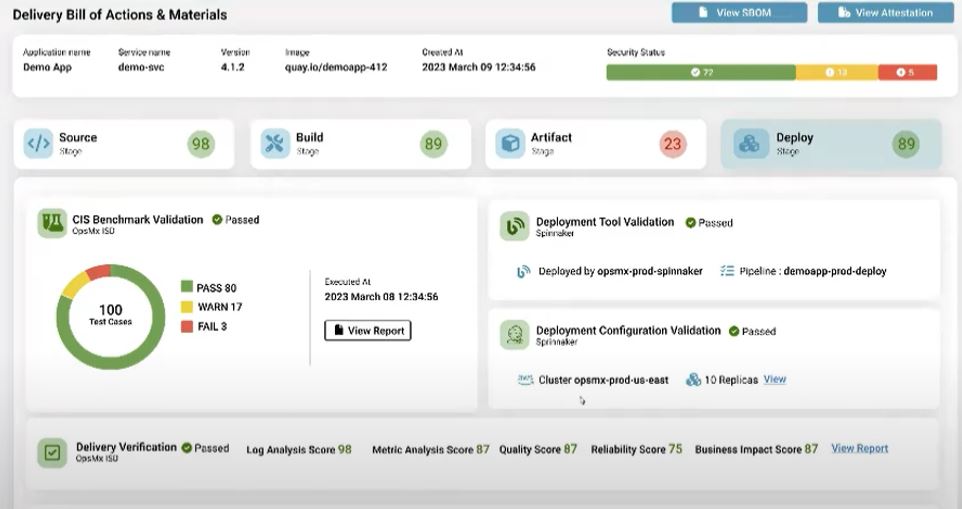
The Delivery Bill of Materials (DeliveryBOM) takes the SBOM one step further to capture a comprehensive, consolidated record of every step in the applications software delivery and deployment process. Security checks, approvals, policy enforcement, and audits are all in one place.
The DeliveryBOM allows DevSecOps and AppSec teams to extend the security oversight beyond code commit and demonstrate policy compliance at scale.
OpsMx is
Trusted By
What is a Delivery Bill of Materials?
The software bill of materials (SBOM) is quickly becoming a requirement for a secure software supply chain. The SBOM, however, only captures what happened at Build. How do you get visibility and ensure compliance for the rest of the application lifecycle, from Build to Production Deployment?
The Delivery Bill of Materials (DeliveryBOM) goes beyond the SBOM to capture the details of the application lifecycle all the way to deployment. The DeliveryBOM enhances software delivery transparency and attestation, and gives visibility over continuous delivery and deployment.
The DeliveryBOM is an integral component of OpsMx Secure Software Delivery solutions. It captures end-to-end visibility into all elements and related actions taken (code analysis and scanning, dependency validation, approvals, etc.) for software delivery and deployment.
What’s Included in a DeliveryBOM?
Deployment Checks and Validations
- Deployment tool validation Configuration validation
- Quality, performance, reliability and business impact scores for a release
- Configuration validation
- Approval validation
- Automated CIS benchmark validation
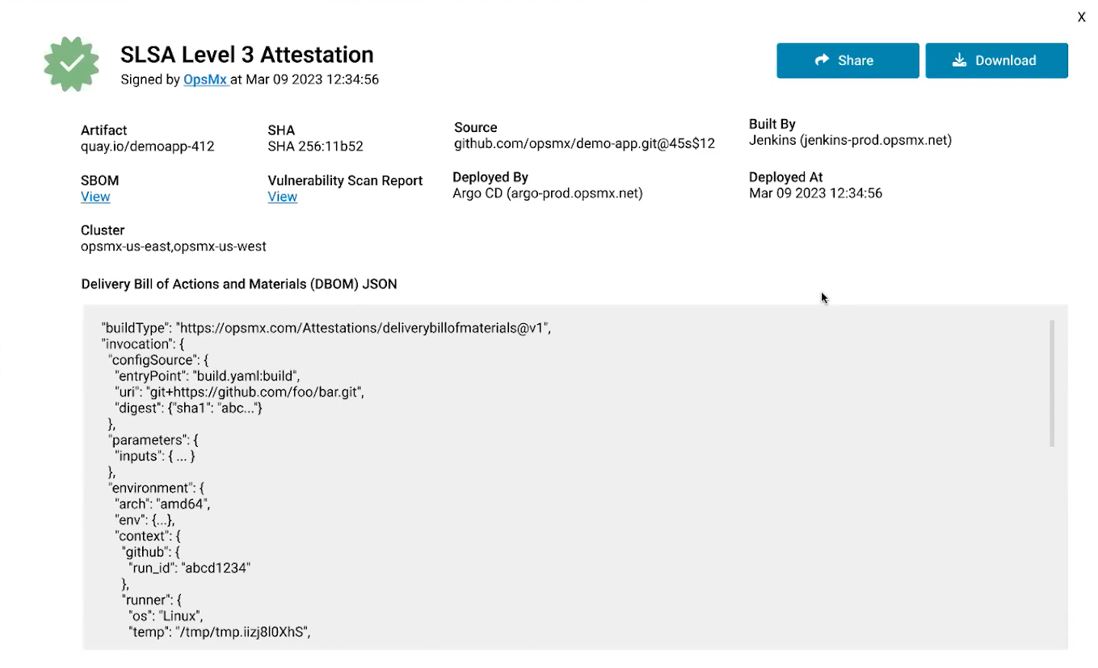
Compliance Policy Enforcement and Audit
- Results of rules library for checks and validations
- Automated SLSA Level 3 attestation
- Complete audit trail with proof of actions for associated incident
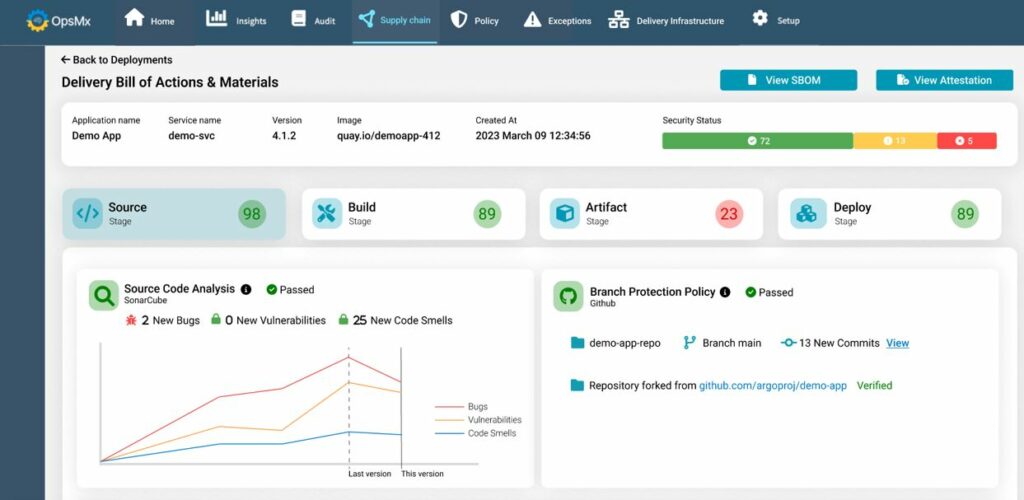
Source Code Security and Vulnerability Assessment
- Centralized code checks and reevaluations
- Automated source code analysis at scale
- Source code provenance and code review validation
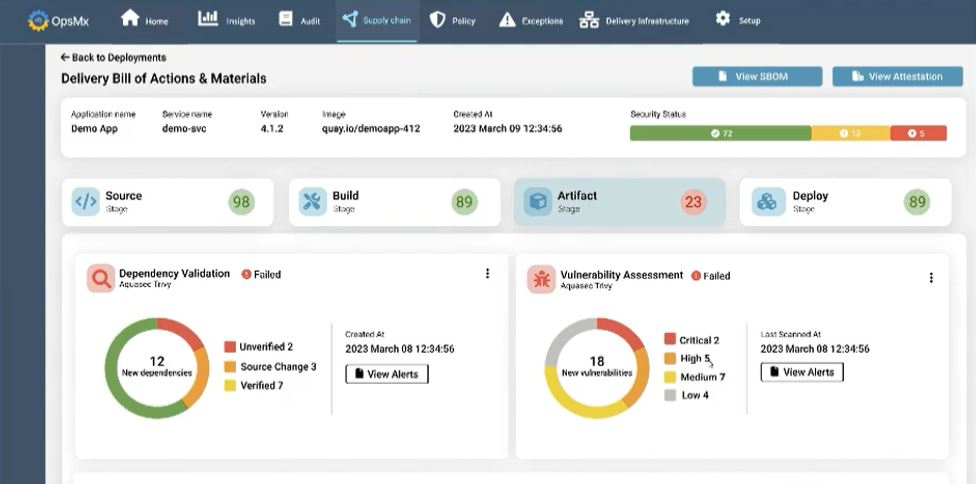
Artifact Validation
- Automated dependency validations for a build (supply chain security, malware protection, cloud security, etc.)
- Dynamic vulnerability tracing (for example, using Aquasec)
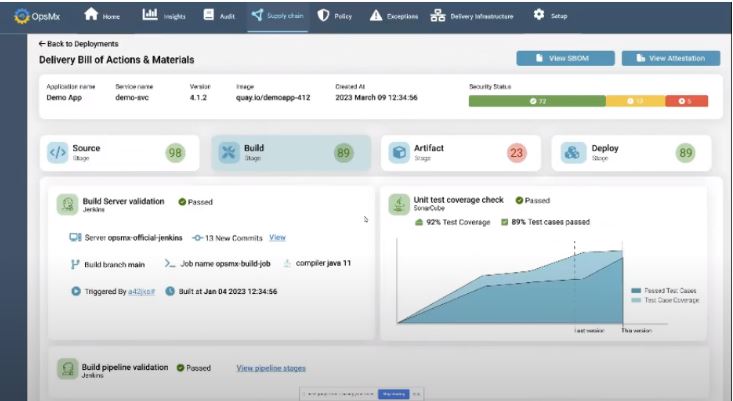
Build Security Validation
- Automated build server validation
- Unit test coverage check and validation
- Build pipelines validation
DevOps Toolchain Integrations
Secure Continuous Delivery Datasheet
Read about secure, automated, and scalable CD solution to reduce risk exposure and bring greater resilience and integrity to your applications
Top Reasons to Consider Deployment Security
Learn how radical changes in the delivery processes introduce new security risks and increase the attack surface.
Tackle the Threat of Software Supply Chain Attacks
Find the comprehensive solution to tackle real-time vulnerability risks and security breaches in your delivery process.