Secured Software Delivery
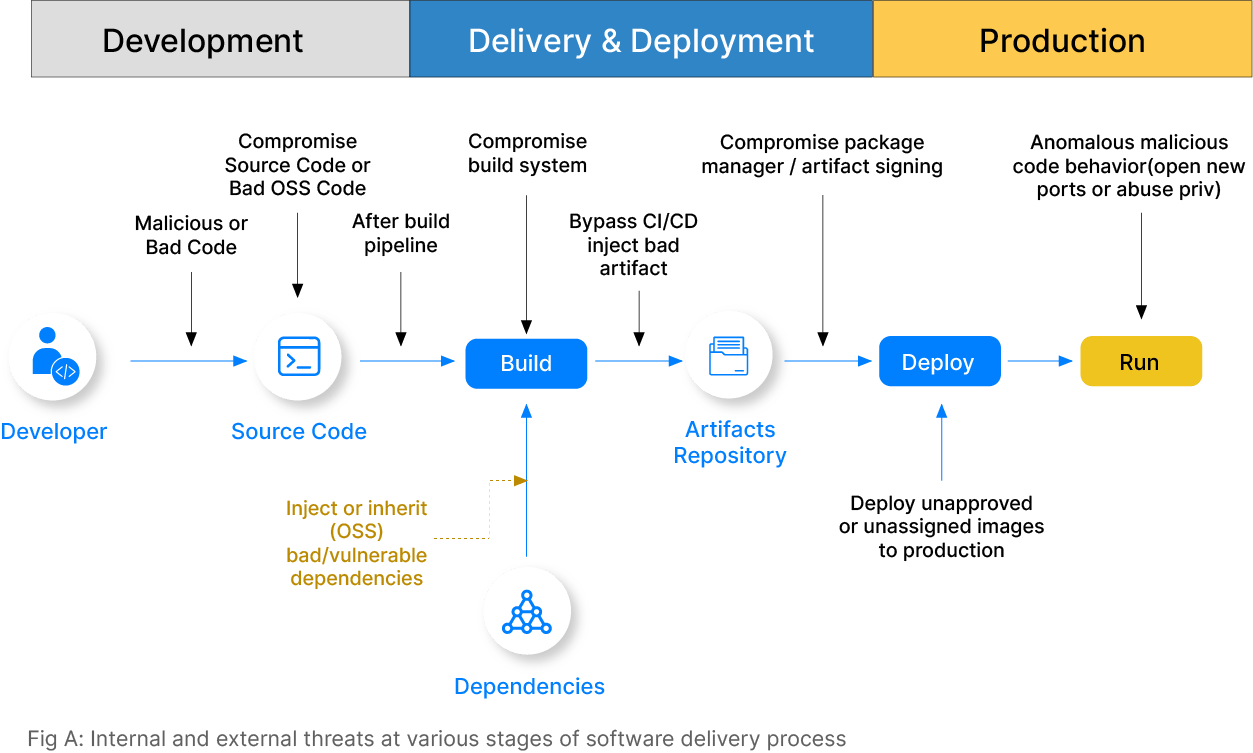
The modern software delivery process (or the CI/CD process) includes many tools, distributed teams, open-source code, and cloud platforms. Constant focus on speed to release software to market, along with the traditional slow and manual security checks, has caused teams to overlook security as an important piece in the software supply chain. Today organizations feel more susceptible to external and internal cyber threats due to the vast attack surface in their applications and the lack of end-to-end governance and risk management.
The software team must secure its software delivery process to avoid vulnerability and security breaches. This can be achieved by preventing the introduction of security issues in the software, discovering and resolving vulnerabilities in production environments quickly, and capturing the deployment bill of materials (DBOM).
Drivers of security for software delivery (CI/CD) process
The speed and scale at which we develop and deliver software have increased exponentially with CI/CD processes. Without proper checks, developers introduce security vulnerabilities, which leads to the risk of business continuity and data theft. The top three drivers which have led to the rise of security in software delivery processes are- Faster delivery processes, Reliance on open-source tech, Rise in cyber-attacks.
Faster & scalable delivery process
DevOps practices have evolved software delivery by integrating development and operations teams, enabling more frequent and automated software releases. Tools such as Spinnaker CD are used to automate software delivery’s build, test, deployment, and feedback stages. Consequently, more changes are released faster and more frequently. However, the increased speed of development and deployment resulted in oversights in security checks and testing in the software supply chain.
Reliance on open source software
Gartner says more than 70% of the application code is estimated to constitute open-source components by the end of 2023. And as open-source and third-party components in software development proliferate, it broadens the potential attack surface. These attacks are increasingly innovative, targeting the most vulnerable parts of the supply chain for easier access and more significant disruption potential. The interconnected nature of modern software ecosystems also means a single breach can have far-reaching implications.
Rise of cyber attacks globally
In recent years, the frequency of software supply chain attacks has drastically increased. As per Gartner, it is projected that 45% of organizations worldwide will have fallen victim to cyber-attacks by 2023. The rate of software supply chain attacks may be higher than reported, as many attacks go undetected or unreported. As third-party software components and faster releases due to DevOps continue to increase, supply chain attacks will likely remain a significant threat to organizations.
Security threats in the software delivery in 2023
GitOps workflow begins by deploying GitOps engines like Argo CD or Flux CD in the target Kubernetes cluster. They are configured with the credentials to access (read-only) the Git/GitOps repository, where application deployment specifications for the cluster are stored.
Diverse toolchain leads to misconfiguration
The delivery process involves multiple tools and technologies, often used by different teams in the CI/CD process. This can lead to misconfiguration and increased complexity, creating security blind spots. A typical example is Kubernetes misconfigurations, which increase the system’s vulnerability. People often use default configurations in Kubernetes, which leads to a security threat because if an attacker accesses a resource, the entire cluster can be easily hacked.
Decentralized teams and multiple pipelines lead to missed detection
The delivery process of distributed systems would include numerous stages, pipelines, and stakeholders interacting with the same systems and infrastructure. Without proper decentralized controls in place, there are chances of skipping important steps such as approvals or reviews, or introducing mistakes in the production systems. Unvetted solutions by teams or individuals, known as Shadow IT, can further compound these risks.
Focus on speed leads to compromise on security checks
Businesses must launch new software or fixes to market to provide a better experience. The primary focus of the CI/CD process is to align with business and delivery software rapidly, which can sometimes sideline security considerations. While DevOps teams excel at making things work, they may need more security expertise from dedicated security teams, resulting in overlooked or underestimated security risks.
Third-party tools libraries can introduce the risk of cyber-attacks
Developers use open-source libraries in their code, and DevOps teams frequently rely on third-party software and services. If all proper checks are not implemented, then it can lead to additional security risks. A notable example is the vulnerability of Log4j, the open-source logging library used by cybercriminals to compromise systems. Suppose security in the code and 3rd party tools, and libraries are overlooked. In that case, it can lead to malware attacks to steal data or supply chain attacks to gain unauthorized access to 3rd party software.
Non-compliance leads to violations and fines
The use of new software or libraries for DevOps brings a lot of benefits without a doubt. However, there are concerns when particular software or components in software are not compliant with regulations such as FIPS or HIPAA or PCI-DSS, GDPR, etc. Non-compliance can result in fines, legal liability, and reputational damage to any organization.
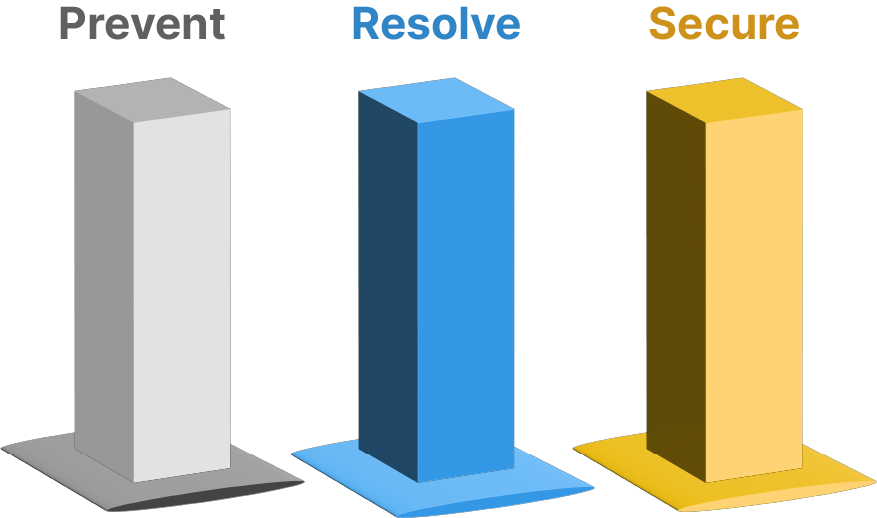
3 Pillar Strategy for Securing Software Delivery
Prevent
Architects and DevOps engineers should consider preventing the introduction of security vulnerabilities in the first place. This can be done through proactive security controls in software delivery pipelines. By implementing proactive security controls, organizations can minimize the risk of vulnerabilities and security breaches throughout the software delivery process.
- Assessment of differences in old and new releases
- Impact analysis of application vulnerabilities (code, libraries, APIs)
- Infrastructure admission controls to ensure a safe target environment for deployment
- AuthN/Z of automated deployment and delivery pipelines
- Automatic policy checks such as deployment window, deployment environment, etc.
Resolve
In the second pillar, we suggest that organizations must have a reliable system for rapidly detecting and mitigating vulnerabilities in their complex and ever-evolving application landscape. The Resolve pillar emphasizes the importance of rapid vulnerability detection and mitigation.
- Timely tracing of vulnerable codes and their environments
- Real-time notification of newly discovered vulnerabilities in changes to the Software Bill of Materials (SBOM)
- Detection and resolution of infrastructure vulnerabilities and adherence to CIS standards
- 360° visibility into each binary in various environments and their sources
Secure
The Secure pillar highlights the importance of traceability, auditing, and exception management. Software delivery teams need clear visibility into their software delivery pipelines, enabling them to maintain a robust, compliant, and secure environment.
- Create a deployment bill of materials (DBOM) with what, how, and where app deployments
- End-to-end visibility into image provenance, build details, dependency differences, and vulnerabilities
- Timely tracking of Git commits, approvals in the delivery process for audit
- Vulnerability exception management system to track when and who allowed known issues and why.
Empowering DevSecOps to secure the software delivery process
DevSecOps is about integrating security and compliance testing into the DevOps pipeline without compromising the speed and agility of continuous delivery. From a team perspective, the collaboration between IT security and the product team ( including development and operations) must be increased to make the software lifecycle agile and responsive.
DevOps teams are empowered in many organizations to implement or handle security in the software development and delivery process. These folks are also often named as DevSecOps. The objective of the DevSecOps team is to identify the best practices, risk mitigation strategies, and the right software to make security a part of the DevOps pipeline. With the empowerment of DevSecOps and the security team, organizations can avoid service disruption, security breaches, and cyberattacks and ensure compliance with privacy regulations.
Benefits of Secured Software Delivery
100% safe release process
100% secured deployment
100% compliance
Additional Read on Secured Software Delivery(SSD)
Getting started with Deploy Shield
OpsMx Deploy Shield offers industry’s first CI/CD solution designed for software supply chain security and DevOps security posture management.
Insights into deployment security
Are you a software delivery leader who wants to understand why deployment security is essential and how to implement it?
How to implement DevSecOps
Are you a DevOps or cloud architect looking to implement DevSecOps in your software delivery process?
Request a demo
Want to learn how OpsMx Deploy Shield can help you implement secure software delivery in your ecosystem?
OpsMx is
Trusted By
Keep up to date with OpsMx
Be the first to hear about the latest product releases, collaborations and online exclusive.