If you are a
- DevOps Manager and care about accelerating deployments, minimising rollbacks and downtime of your applications,
- DevSecOps Manager and care about preventing vulnerabilities reaching the production environment,
- Site Reliability Engineering (SRE) Manager and care about high performance and exceptional user experience on your services,
- Compliance and Risk Manager and care about achieving near-100% compliance,
- Auditor and intend to eliminate manual audits and have reports with proof points at a press of the button,
Then, this blog is for you.
If you care about above and if you are doing it in the right way then I believe, like many of our tier-1 or tier-2 customers, you are able to:
- Reduce risks and penalties due to non-compliance
- Accelerate speed of software delivery by 10x
- Reduce incidents by 80%
- Reduce MTTR by 40%
- Achieve 99999 resiliency and reliability
- Reduce operational costs by 40%
If not, then you need OpsMx Deployment Firewall!
What is “A Bad Code”
Developers may think that they have written the best possible code, however the reality changes when:
- DevSecOps manager notifies security vulnerabilities in the code they have written which may lead to breaches and non-compliance. A vulnerable code may lead to significant impact to the business with possible financial penalties.
- Compliance or Risk manager notifies a policy violation or non compliance due to code related issues resulting in delays in the software delivery. This leads to delays in taking mission critical features to production.
- SRE manager notifies memory leaks, or hogging threads resulting in transaction failures or high response times. A bad code resulting in performance issues may lead to downtime and unfavourable user experience resulting in loss of revenue.
- DevOps manager notifies frequently failing pipelines or specific stages due to code issues. This not only impacts the performance of overall software delivery workflow but leads to significant delays and often expensive rollbacks.
What is a Deployment Firewall?
Deployment Firewall in a layman’s language is a firewall that prevents vulnerabilities and issues from going to staging or the production environment. In short, it just keeps bad code out!
From an architectural standpoint it’s a logical layer that sits between the code that intends to be deployed and the deployment destination. This logical layer essentially requires 3 things to help you achieve all of the above –
- Set of rules (policies),
- Data (from your devops tool chain), and
- Enforcement engine to orchestrate and enforce policies.
How Deployment Firewall Works
Deployment Firewall can be understood from the illustration below.
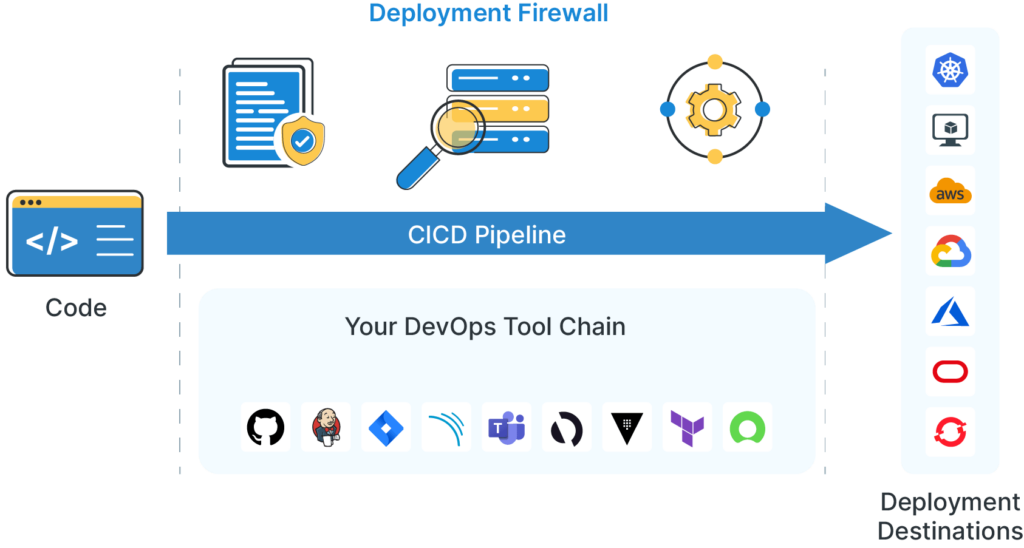
The Deployment Firewall is an integral component of OpsMx Secure Software Delivery. Deployment Firewall seamlessly integrates with your existing DevOps tool chain and is able to sit alongside listening to these tools, listening to your inflight-workflow and is able to orchestrate and enforce policies from deployments or any other stage in your CI/CD pipeline or a workflow.
For a DevSecOps Manager
A deployment firewall can prevent security vulnerabilities from reaching production. This happens by enforcing security policies as a prerequisite before any production deployment. OpsMx currently supports a vast variety of security frameworks and has a library of rules (prebuilt policies that can be reused and even modified depending upon specific needs).
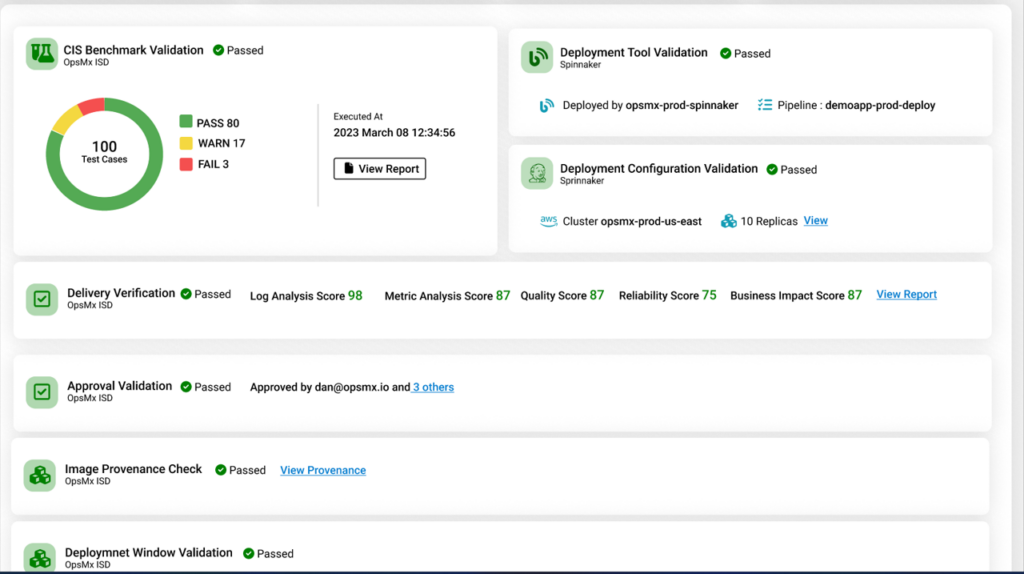
The deployment firewall can normalize and analyze the results from your existing scanning tools (SAST & DAST) to let you know if there’s any vulnerability in your code but more importantly use this data to enforce data-driven policies. Besides this, it can also help you to understand if any third party library (as a part of your overall package) poses a security threat. The Deployment Firewall is not a scanning tool however the differentiation comes in the form of automated analysis and automated decisions and compliances that are associated with the scanning results. More so, you may need proof-points for the audit reports which OpsMx Secure Software Delivery offers at the press of a button.
Another important application of Deployment Firewall is that when a new vulnerability is reported, you can enforce a real time rule to stop all deployments containing the affected packages/ artifacts. As in the case of recent Log4j vulnerabilities.
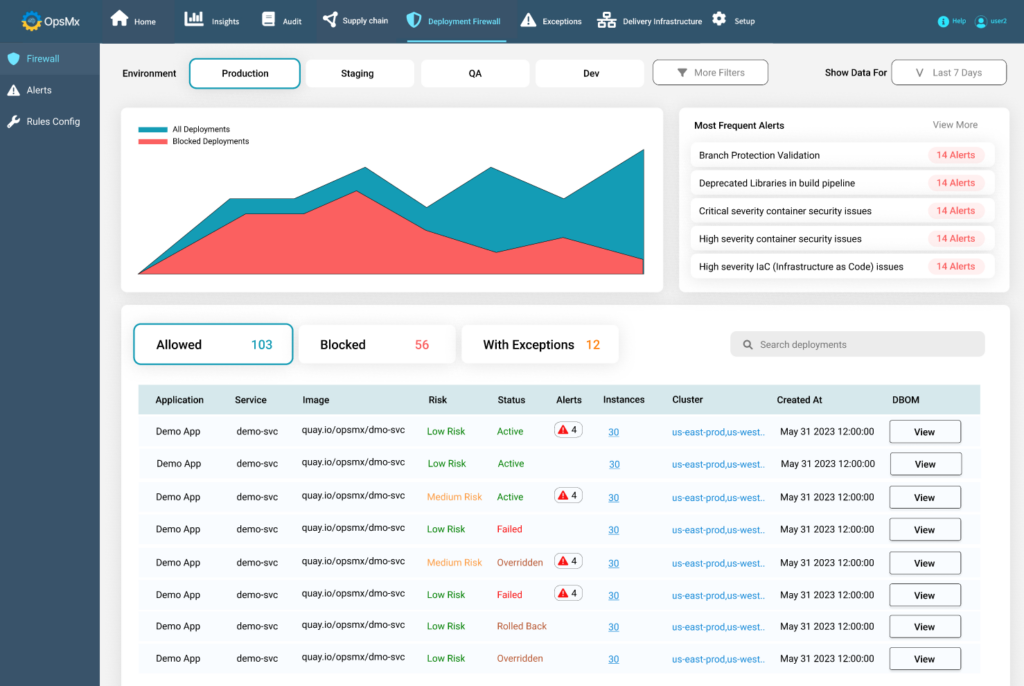
OpsMx Deployment Firewall is extensible to other use-cases that a DeSecOps Manager would care about. For example, Application security posture management, vulnerability tracing and exception handling, attesting artifacts for deployment. You may want to read more to get insights into the overall capabilities of OpsMx Secure Software Delivery.
For SRE and Performance Manager
Automated verification, for test / staging deployments and canary analysis are critical stages for ensuring the deployments are successful and that there’ll be no issues or unfavorable user experience for the load on production or the staging (with load test) after deploying the software.
Currently SREs spend hours to diagnose and detect performance issues relying on the alerts and notifications. This is as good as the instrumentation profile and configurations set by a SRE manually. And, manual activities are error prone and inconsistent as far as reviews are concerned.
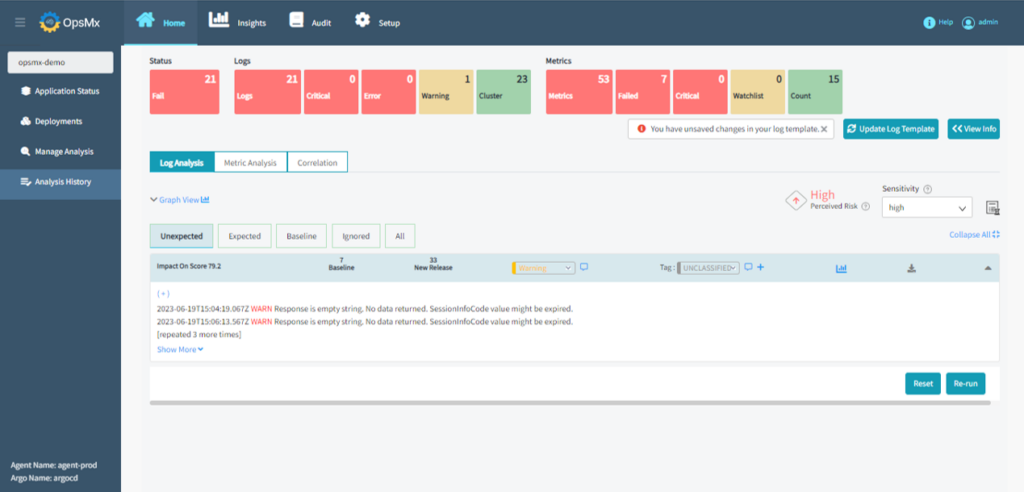
The automated verification analyzes both metrics and logs using AI/ML driven algorithms and determines a verification / performance score. This is combined with automated decisions resulting in progression in deployment stages in case of canary if the verification score is above pass score or may result in a rollback in case verification fails. The full value of automated verification is derived if a user is deploying the software by using deployment stages out of OpsMx Secure CD.
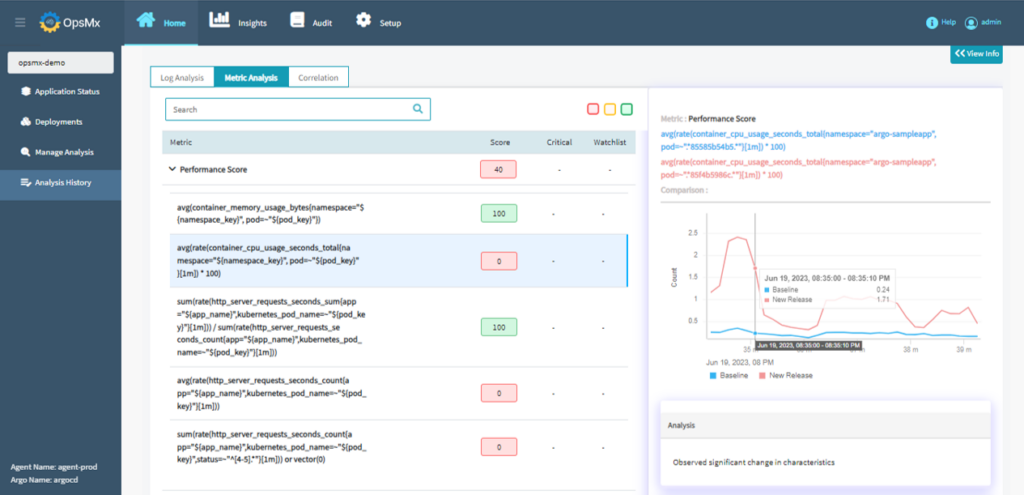
OpsMx Secure CD seamlessly integrates with your existing observability or log monitoring tools and provides automated decisions based on AI/ML driven analysis. This also gives you the ability to enforce a compliance policy – for example – do not proceed with the deployment in case the verification score is less than 80%. Read more about continuous verification and automated risk assessment for advance deployments.
For Compliance or Risk Manager
The Deployment Firewall helps the compliance officer or a risk manager to enforce rules and automate compliance as a part of secure SDLC initiative.
The prepackaged set of rules or policies within the Deployment Firewall are not restricted to:
- Security,
- Performance or Resiliency,
- Quality,
- Regulatory, and
- Business or industry standards compliance
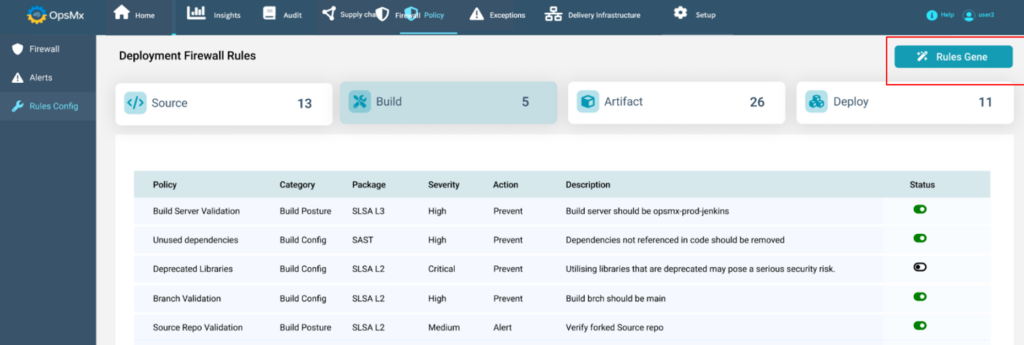
Before the deployment stage policy enforcement triggers the data collection and analysis from the tech tool ecosystem and derives a decision making conclusion in the form of policy violation or policy obedience.
For example, is your code HIPAA compliant? Or,
Are you compliant with specific NIST-800-53 policies? Or,
There’s a complete document on how to achieve SDLC compliance automation leveraging your existing CI/CD pipelines and policy enforcement.
For Audit Manager
Deployment Firewall provides auto generated audit reports (along with the proof points) on policy executions, violations and obedience. It also determines a smart diff – a provenance check.
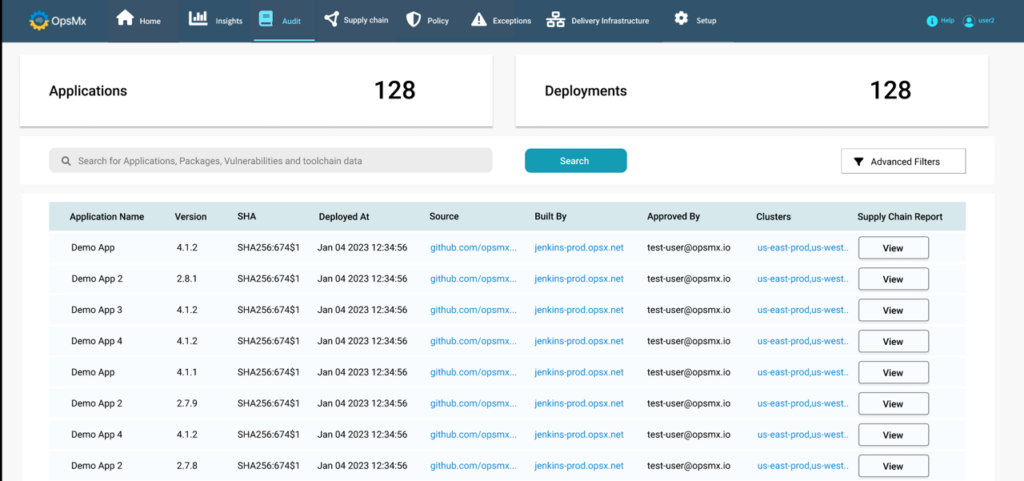
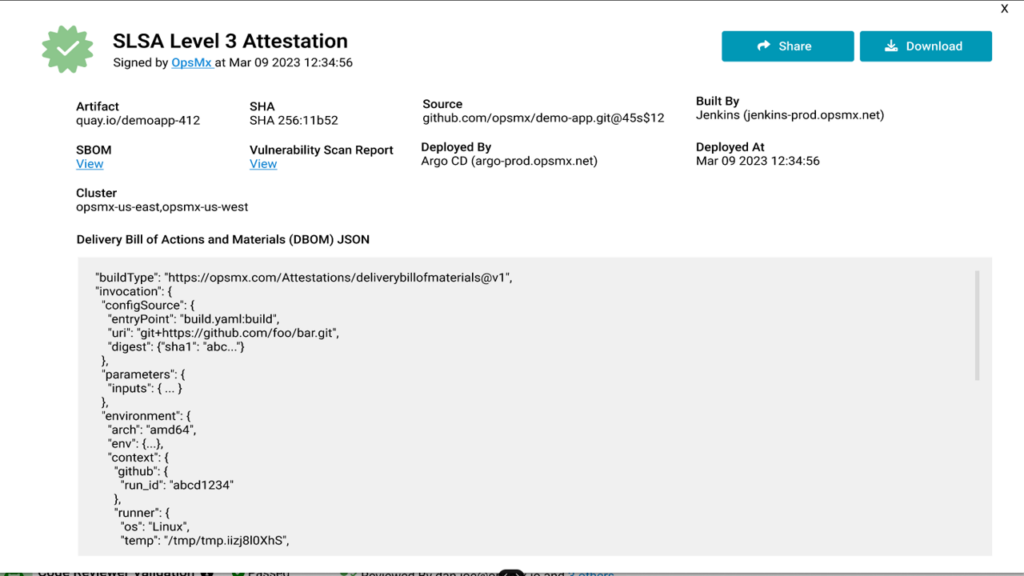
Another one provides validation and proof points whether artifacts getting deployed are attested?
For DevOps Manager
And for all the stakeholders listed above, the Deployment Firewall comes with a fully functional dashboard with a 360 degree view of what’s happening in terms of operations – execution and performance of your pipelines and specific tasks with real-time insights and controls.
More importantly, as a DevOps Manager you know that you’ve deployed a package that was meant to be deployed.
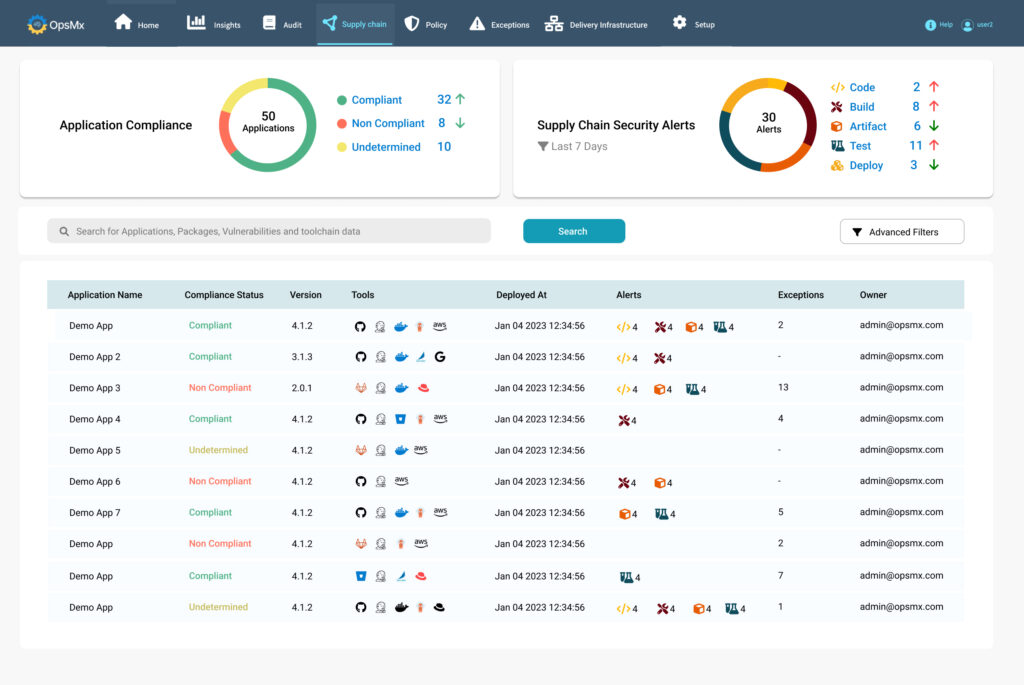
Deployment Firewall puts DevOps and DevSecOps in the driving seat. Deployment Firewall is an important prerequisite to implement DevSecOps. If you intend to prevent security vulnerabilities and compliance issues from going to the staging or the production then Deployment Firewall is a must have.
You may want to read more on how OpsMx Secure Software Delivery enables a scalable model for secure and compliant continuous software delivery leveraging your existing devops assets.
Talk to one of our Top Secure CD experts to obtain a blueprint of successful secure software delivery for your enterprise!


0 Comments