I’ve spoken to quite a few DevSecOps experts and implementers over the past couple of months and there’s been a commonality in terms of their priority initiative – They are looking to implement enterprise-wide compliance for their software delivery life cycle leveraging their existing CI/CD solution. Another way to rephrase this is to collect proof points or the data, which validates that the best practices are getting translated into actionables within the enterprise-wide SDLC process.
Some of them have been working for quite some time to achieve this, however to have a standard centralized model that works for all engineering groups within an enterprise is not straightforward.
Having said that, it is not that difficult either. All you need is the right set of minimum required capabilities in your existing devops tool chain, or bridge the gaps by bringing in an additional layer on top of these products.
At bare minimum following are the three important capabilities needed to achieve enterprise-wide compliance management for SDLC:
- Policy enforcement / orchestration mechanism
- Integrate and execute policy gate with specific devops tools / jobs
- Pre-packaged, reusable, identified set of compliance rules / policies
- Generate audit reports for policy compliance with press of a button
Policy Enforcement / Orchestration
This is the key capability that allows you to select a policy or a compliance rule and orchestrate / execute that policy at a specific stage of your SDLC in the form of a policy stage within your existing CI/CD pipeline.
A common example is that you do not want the release or the deployment to happen if there are security vulnerabilities identified in the package and you would like to enforce it as a policy. To achieve this you need to first identify the right policy or select one from a pre-packed list of policy / compliance rules. We will separately discuss about the types of prepackaged policies or compliance rules available in OpsMx Secure Software Delivery (SSD).
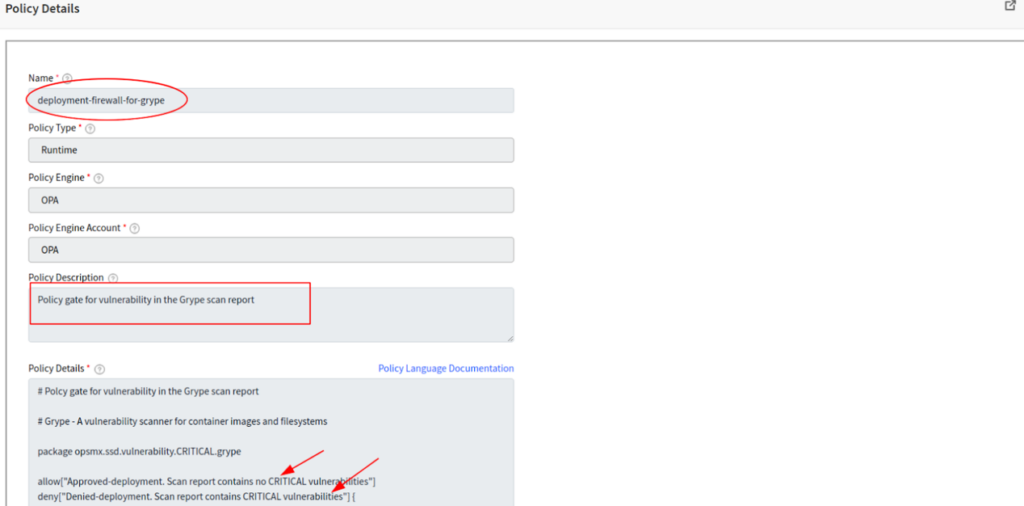
You can also make use of OpsMx Rules Genie to easily define your own custom policy and enforce it using SSD.
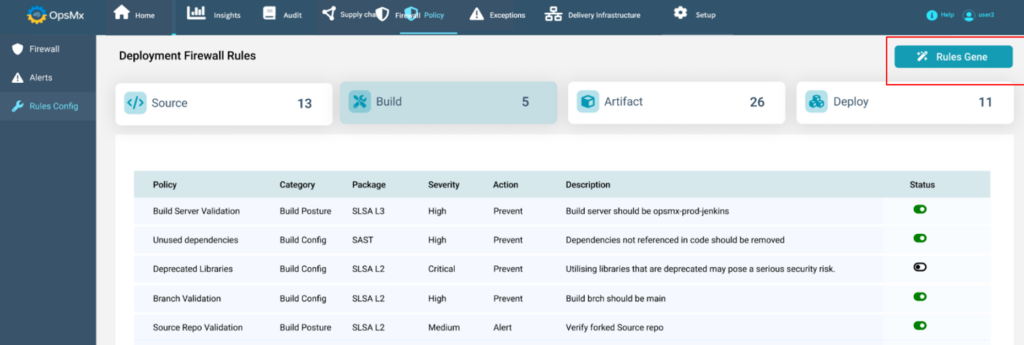
Let ‘s say you are using a Jenkins pipeline to deploy and you want to enforce a policy before deployment to confirm any security vulnerabilities. The user is supposed to trigger the Jenkins deployment job but as a DevSecOps implementer you want to enforce that no deployment happens without verifying the security vulnerability status. To achieve this, you can simply insert a deployment firewall that will run appropriate rules and prevent vulnerabilities from going to staging or the production.
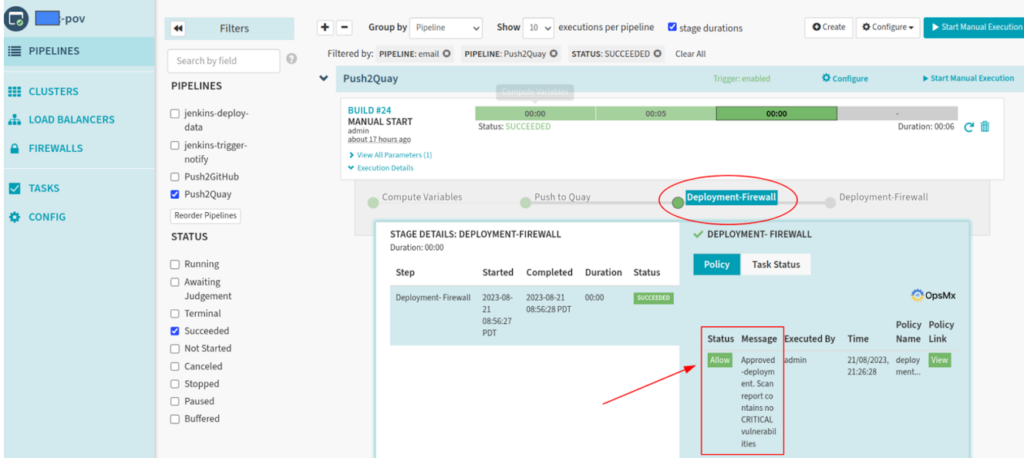
The policy violation would trigger the termination of the pipeline and prevent it from progressing to the next stage and send notifications to the relevant DevOps / DevSecOps or engineering members.
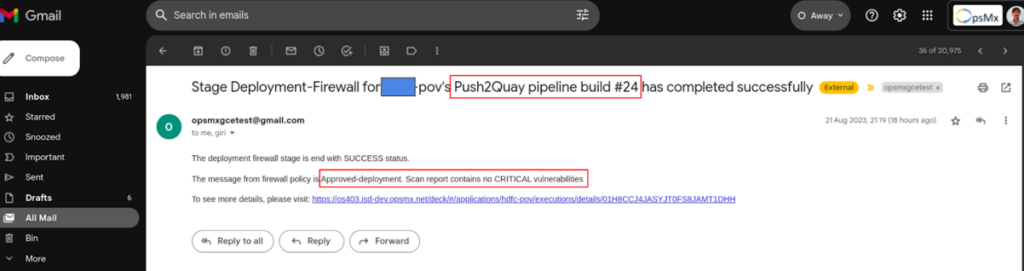
This also allows you to automate governance by ticketing any such incidents in your governance tools like Jira or ServiceNow for audit reporting purposes with proof points.
Integrate With Your Existing DevOps Tool Chain To Enforce Policy At Specific Stages
To implement the above mentioned use case, you need integrations with Jenkins, Jira / ServiceNow, Scanning Tool/s, Notification tool (email / MS Team) and most importantly your CI/CD orchestration tool.
Similarly, to set enterprise-wide compliance specific to roles and responsibilities you need to integrate to other tools such as git repository or the artifact tool for developers, observability and log monitoring tools for SREs and SAST or DAST tools for DevSecOps.

If you have to do it by writing scripts or code, you’ll not be able to achieve a scalable model which is flexible enough to work through the future requirements.
You basically require an out of the box integration mechanism with the policy orchestration and enforcement tool that sits besides your existing devops tools and allows you to integrate without having the need to write any scripts or code. This will help you to leverage the data coming out of these tools and enforce data-driven policies.
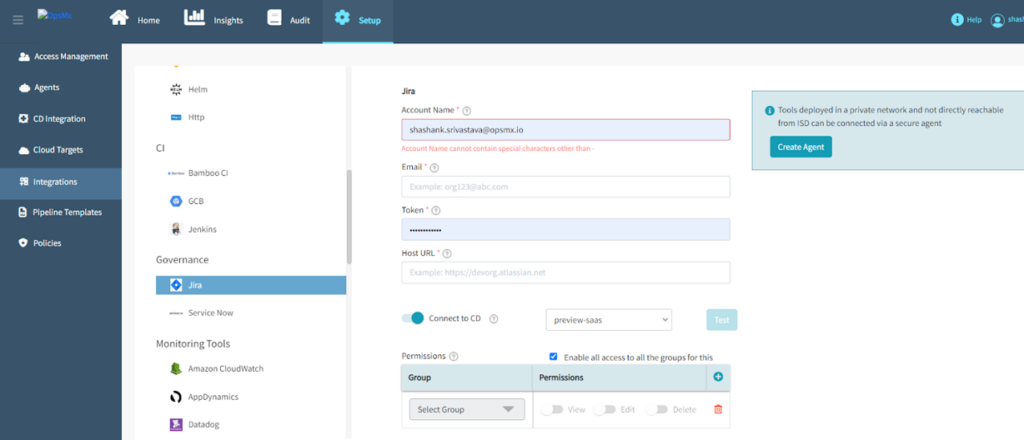
For example, a policy that allows you to restrict a software release if there are P1 or P2 open. This can only happen if you are able to integrate to your ticketing system and execute a policy with run-time parameters that check if there are any P1 or P2 open for that particular build or a branch. Or, let’s say you want to implement Separation of Duties as a part of SOX implementation. You can definitely do this as well.
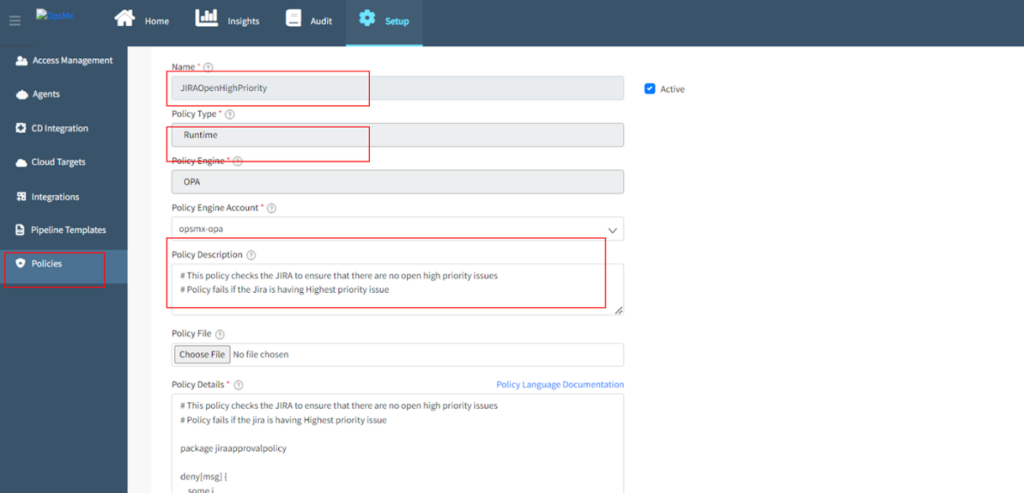
Pre-packaged, Reusable, Identified Set of Compliance Rules / Policies
You may want to refer to a separate blog written on the list of compliance rules or policies that are available out-of-the-box or prepackaged with OpsMx SSD.
But at a very high-level the policies or compliance rules vary from enterprise to enterprise depending upon their nature of operations, geography or countries for specific regulatory mandates, and industry vertical they operate in.
Some of the common prepackaged list of policies included in SSD and are not limited to:
- NIST-800-53 Policies
- SOC 2
- GDPR
- CIS Benchmarks
- SLSA Level 1-4
Generate audit reports for policy compliance with press of a button
Last but not the least, the ability to generate a report on policy executions and violations along with the proof points in the most critical one.
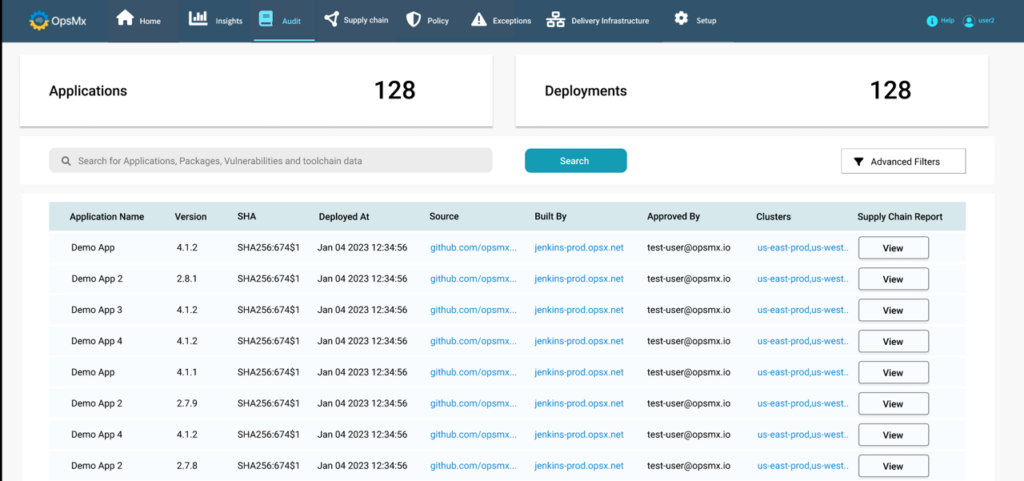
This not only serves the purpose of audit readiness but allows to reduce the MTTR and provides the ability to anticipate and prepare for outcomes.
Besides policy audit you can also get the ability to not only enforce policy for compliance but also generate reports for actionable intelligence. As an example, you can generate reports for attesting artefacts in the form of an audit delivery attestation report.
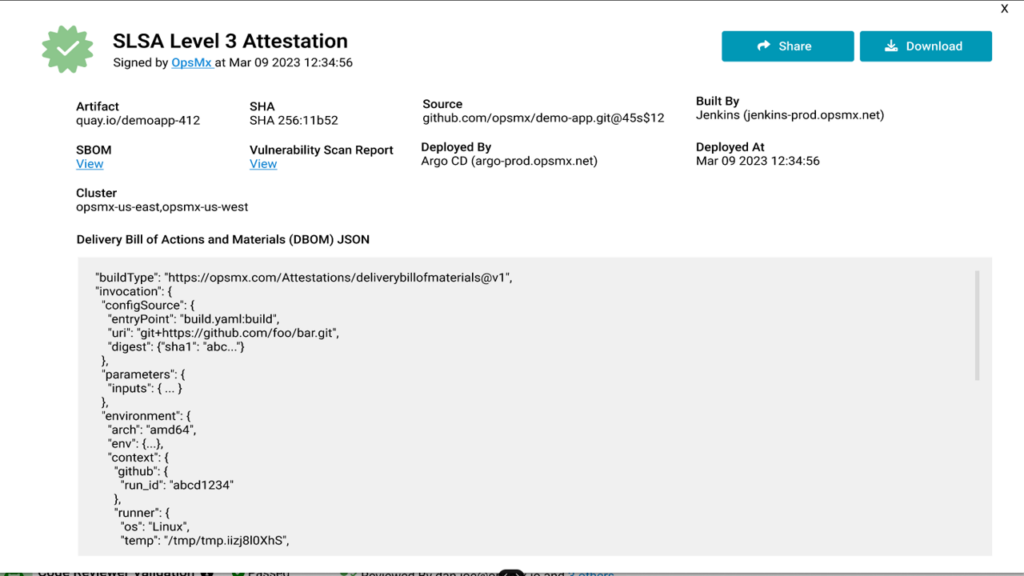
Or even generate a CIS benchmark validation report from the OpsMx SSD Deployment Firewall.
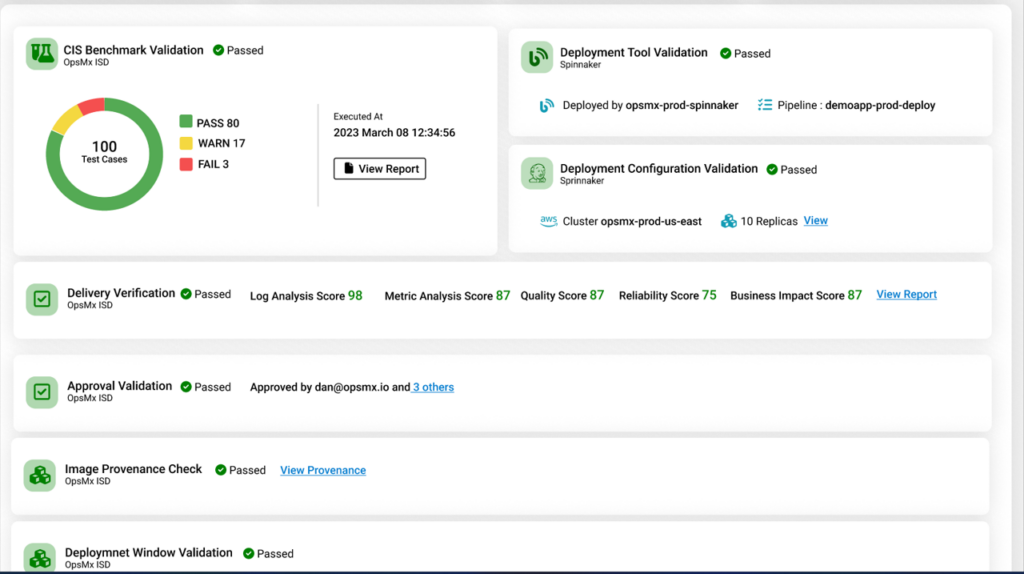
There are several benefits that come along with policy enforcements besides a near-100% compliance, for example:
- 80% less product issues or vulnerabilities
- 60% reduction in MTTR
- 40% reduction in cost of operations / remediation
Getting Started With SDLC Compliance Management, Next Steps
If you are looking to implement enterprise-wide compliance automation for your SDLC, OpsMx Secure Software Delivery (SSD) can get you started in minutes.
It comes along with all the required capabilities as mentioned and demonstrated above to reduce your implementation time for enforcing and achieving a near-100% compliance in your software release and delivery processes.
For more details please contact us to talk to one of our top Secure CD experts.



0 Comments