Amidst this growing tension around emerging cyber threats, one of the hottest topics in the software industry is ASPM (Application Security Posture Management). And rightly so, organizations must have a conversation around their ongoing AppSec practices and how to improve their security posture further.
Need for a strong AppSec posture
According to this report by Accenture, $13 million was the average cost to organizations that fell prey to cybercrimes. And with newer sophisticated tools and techniques, the attack only gets more fierce. However, if strong AppSec posture was in place, these organizations could have prevented such damage and defended themselves against cybercrimes such as SQL injection, cross-site scripting (XSS), unauthorized access, and malware injections.
Infact, a strong AppSec posture not only helps organizations comply with industry regulations such as GDPR, HIPAA, PCI DSS, but also acts as a strong foundation to handle confidential information, such as personal and financial data ensuring integrity, confidentiality, and data privacy.
Now this is a good time to introduce the role of ‘compliance’ in AppSec posture management.
What is Compliance?
In simple terms, ‘Compliance’ is the act of adhering to rules, regulations, standards, or guidelines established by external authorities or internal policies within an organization. Thus, ‘being compliant’ means that any process, product, or service offered by an organization meets industry standards or obligations.
Most large enterprises are driven by mandates requiring them to operate under certain constraints. These are either enforced by the industry they are operating in, or by the organization itself. There are numerous benefits associated with following them such as:
- Legal Obligations: Failure to comply with relevant laws and regulations can result in legal penalties, fines, lawsuits, or regulatory sanctions.
- Risk Management: Compliance helps mitigate risks associated with non-compliance, such as financial loss, reputational damage, operational disruptions, or data breaches.
- Trust and Reputation: Demonstrating compliance builds trust and credibility with customers, partners, investors, and other stakeholders, enhancing the organization’s reputation and brand value.
- Operational Efficiency: Adhering to established standards and best practices improves operational efficiency, quality assurance, and process consistency within the organization.
- Competitive Advantage: Compliance with industry standards and regulations can provide a competitive advantage by demonstrating commitment to quality, security, and responsible business practices
‘DevSecOps’ and the role of Compliance in Software Delivery
‘DevSecOps’ and ‘Compliance’ go hand in hand. Even though they are very different concepts by definition, they intend to address the same problems, i.e. ensuring/ enforcing security into software development and deployment.
Most readers would be familiar with the concept of ‘DevSecOps’, if not refer to this blog.
The purpose of DevSecOps is to bring the security team closer to the DevOps team. The purpose of compliance is to ensure that security regulations are adhered by the DevOps team. Since a DevOps process is a complex puzzle with numerous moving parts, finding cohesion between developers, operators(Ops), and security pros. is a constant challenge.
In an ideal world, having ‘DevSecOps’ and ‘Compliance’ processes can be considered exemplary from a security point of view. However if you observe closely, the common theme in such organizations is security teams constantly putting out fires in the nth minute and devops teams always in a battle against time.
‘DevSecOps’ and ‘Compliance’ processes in silos is simply not enough. The secret sauce is ‘Automating Compliance into DevSecOps’.
Automating Compliance in DevSecOps
In order to achieve both agility and security in software delivery, compliance must not just be embraced, it must be ‘automated’. DevSecOps compliance automation not just streamlines security standards, but also eliminates bottlenecks resulting from manual checks.
This progressively leads us to the next question – how do we automate compliance in DevSecOps?
- Implement Compliance as Code
- Automate Compliance Checks
- Continuous Monitoring and Auditing
- Policy Enforcement
Implementing Compliance-as-Code
‘Compliance-as-Code’ is the process of codifying compliance requirements and security controls into configuration files, automation scripts, and infrastructure templates using the principles of infrastructure as code (IaC) and policy as code (PaC). This can help define compliance rules programmatically and enforce them consistently across development environments.
Automate Compliance Checks
By automating compliance checks, organizations can identify security issues and non-compliant configurations early in the development process, and thus reduce the risk of non-compliance. This not only speeds up the compliance verification process, but also eliminates bottlenecks arising from manual checks.
Continuous Compliance Monitoring and Auditing
Monitoring tools and Security Information and Event Management (SIEM) systems can be used to collect and analyze security-relevant data, detect deviations from compliance standards, and trigger alerts or automated responses as needed. This is one such mechanism to track compliance status and security posture across DevSecOps environments in real-time.
Policy Enforcement
Automated policy enforcement mechanisms ensure that compliance controls are enforced consistently across development environments. Various tools and frameworks can be used to enforce policies with the help of declarative configurations, role-based access controls (RBAC), and the principles of least privilege.
Now that we’ve understood the importance of ‘automation’ in DevSecOps Compliance, let me address the popular Compliances that organizations struggle with and how OpsMx can help automate those compliances into their software delivery processes.
Types of Compliance in Software Delivery
Depending on the industry an organization is operating in, or the geography or specific business activities, an organization may need to adhere to different compliances. Here are some common compliance types:
- Legal compliance
- Regulatory compliance
- Standards-based compliance
- Other compliance types:
- Corporate Compliance
- Financial compliance
- Legal compliance
- HR compliance
Legal Compliance
Legal compliance involves adhering to laws, statutes, and judicial decisions that govern various aspects of business activities. Compliance with legal requirements ensures organizations operate within the boundaries of the law.
For example: the General Data Protection Regulation (GDPR) sets standards for data protection and privacy in the EU.
Regulatory compliance
Regulatory compliance involves adhering to specific rules, regulations, and standards imposed by regulatory bodies or government agencies within a particular industry or sector. Regulatory requirements are often industry-specific and may be aimed at protecting public interests, ensuring consumer safety, promoting market stability, or maintaining industry standards.
Examples include compliance with the Health Insurance Portability and Accountability Act (HIPAA) in healthcare and the Payment Card Industry Data Security Standard (PCI DSS) in the financial sector.
Standards-based compliance
Standards-based compliance involves conforming to industry standards and guidelines established by regulating bodies or professional organizations. These standards set benchmarks for quality, security, and performance in their respective domains. Adhering to these standards ensure consistency, safety, and interoperability, within organizations and across industries.
Examples include ISO 9001 for quality management, ISO/IEC 27001 for information security management, and NIST 800-53 for federal information systems security controls.
Other notable Compliance types
I will not be going into much details about the other compliances as their scope is not that relevant in the context of software delivery. But just to touch base upon it briefly, compliance standards are also applicable in other aspects of IT such as Corporate Compliance, Financial compliance, Legal compliance, and HR compliance.
How can OpsMx help you stay compliant during Software Delivery?
Compliance frameworks are essential for organizations to establish effective governance, risk management, and compliance (GRC) programs. These frameworks help businesses identify, assess, and manage risks while ensuring that they operate within the legal and regulatory boundaries applicable to their industry.
OpsMx Secure Software Delivery (SSD) has inbuilt security modules that convert these frameworks and rules into Policy as Code (PaC) format, which is machine readable. In parallel to this, OpsMx SSD also collects events and data by integrating with other DevOps tools across the SDLC.
The PaC checks mentioned earlier are performed on top of this incoming data. And results from the evaluation get published as part of our Delivery Bill of Materials (DBOM) report as well as in the ‘Open Security Issues’ section in the SSD dashboard. Refer to the below screenshot.
OpsMx supports the following compliance frameworks as part of our Secure Software Delivery offering:
- NIST 800-53
- FedRAMP
- OpenSSF ScoreCard
- OWASP Top 10 CI CD Security Risks
- NSA CISA Top 10
- MITRE-ATT&CK
- CIS Benchmark Kubernetes
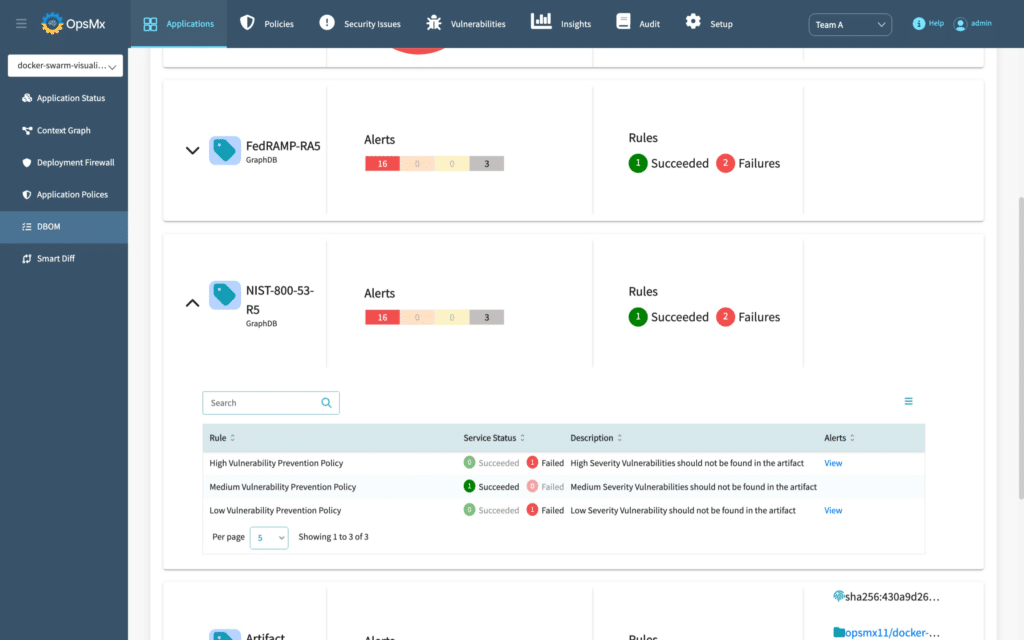
NIST 800-53
NIST 800-53 compliance covers aspects of information security, including access control, incident response, cryptography, configuration management, and more. Examples of NIST 800-53 policies supported in OpsMx SSD:
- Branch Deletion Prevention Policy
- Branch Protection Policy
- Bot User should not be an Org Owner
- C-0054 – MITRE – Cluster internal networking
Read our documentation for more information.
Here’s an example of OpsMx SSD evaluating a deployment against policies defined in accordance with the NIST 800-53 framework.
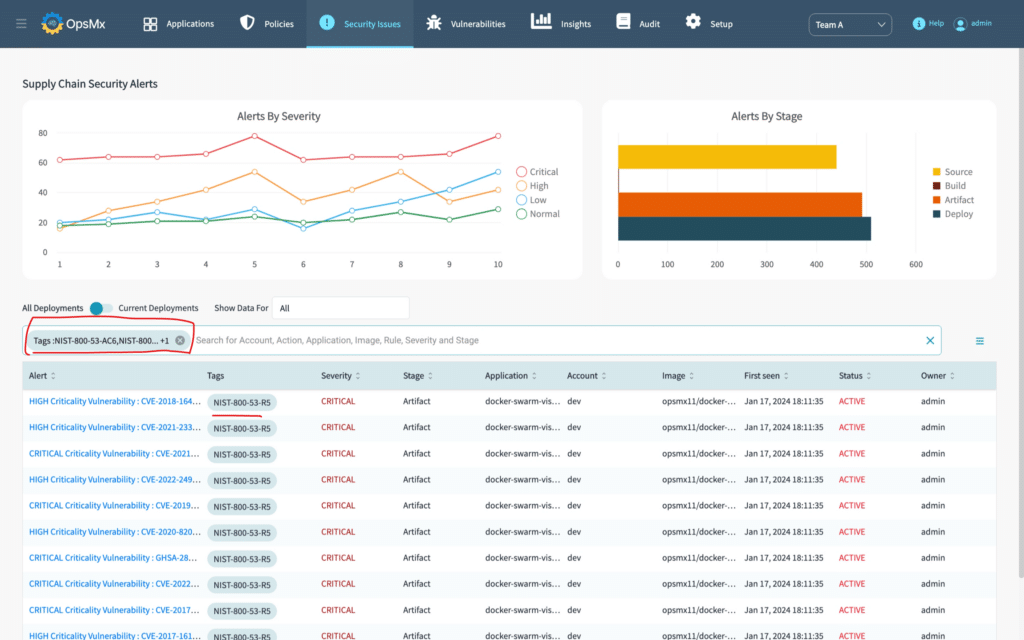
FedRAMP
The Federal Risk and Authorization Management Program (FedRAMP) is a U.S. government program designed to ensure that cloud services used by federal agencies meet a consistent set of security and privacy standards. This framework when integrated in SSD, gets converted to code format. The policies created based on this framework prompts an alert or prevents the deployment if the rule fails.
Examples of FedRAMP policies supported in OpsMx SSD:
- Block Container Without Limits
- Block Container Without Request Limit
- Block Undefined Container Ratios
- High Vulnerability Prevention Policy
- Low Vulnerability Prevention Policy
OpenSSF ScoreCard
Open Source Security Foundation (OpenSSF) is an industry collaboration focused on improving the security of open-source software. This framework, when integrated in SSD, gets converted to code format. The policies created based on this framework prompts an alert or prevents the deployment if the rule fails.
Examples of OpenSSF policies supported in OpsMx SSD:
- Open SSF Binary Artifacts Policy
- Open SSF CI Tests Policy
- Open SSF Packaging Policy
- Open SSF Signed Releases Policy
- Open SSF Token Permissions Policy
OWASP Top 10 CI CD Security Risks
OWASP (Open Web Application Security Project) Top 10 list focuses primarily on web application security risks rather than CI/CD (Continuous Integration/Continuous Deployment) security risks. Examples of OWASP CI CD policies supported in OpsMx SSD:
- Prohibited use of unspecified package versions
- Refrain from running pipelines originating from forked repos
- Untrusted Deployment via Configuration Drift
- Open to merge public repositories for code utilities
NSA CISA Top 10
The NSA concentrates on signals intelligence and securing national security systems, while CISA is primarily responsible for enhancing cybersecurity resilience across government and critical infrastructure sectors and coordinating cybersecurity efforts at the national level.
Examples of NSA CISA policies supported in OpsMx SSD:
- C-0068 – NSA – PSP enabled – Pod Security Policies enable fine
- C-0067 – NSA – Audit logs enabled
- C-0058 – NSA – CVE-2021-25741
MITRE-ATT&CK
MITRE ATT&CK compliance framework is a standardized set of regulations or requirements that organizations must adhere to improve cybersecurity defenses, threat detection, and incident response. This framework, when integrated in SSD, gets converted to code format. The policies created based on this framework prompts an alert or prevents the deployment if the rule fails.
Examples of MITRE-ATT&CK policies supported in OpsMx SSD:
- C-0067 – MITRE – Audit logs enabled
- C-0068 – MITRE – PSP enabled
- C-0069 – MITRE- Disable anonymous access to Kubelet service
- C-0070 – MITRE – Enforce Kubelet client TLS authentication
- C-0035 – MITRE – Cluster admin binding
CIS Benchmark Kubernetes
The Center for Internet Security (CIS) provides benchmarks and best practices for securing various technologies, including configuring and managing Kubernetes clusters to enhance the application security posture. This framework, when integrated in SSD, gets converted to code format. The policies created based on this framework prompts an alert or prevents the deployment if the rule fails.
Examples of MITRE-ATT&CK policies supported in OpsMx SSD:
- CIS – Compliance Score – Range: 0-30
- CIS-1.1.1 Ensure that the API server pod specification file permissions are set to 600 or more restrictive
- CIS-3.2.1 Ensure that a minimal audit policy is created
- CIS-5.3.1 Ensure that the CNI in use supports Network Policies
- CIS-5.7.4 The default namespace should not be used
About OpsMx
OpsMx is a leading innovator and thought leader in the Secure Continuous Delivery space. Leading technology companies such as Google, Cisco, Western Union, among others rely on OpsMx to ship better software faster.
OpsMx Secure CD is the industry’s first CI/CD solution designed for software supply chain security. With built-in compliance controls, automated security assessment, and policy enforcement, OpsMx Secure CD can help you deliver software quickly without sacrificing security.
OpsMx Deploy Shield adds DevSecOps to your existing CI/CD tools with application security orchestration, correlation, and posture management.

0 Comments