In my previous blog, I explained what is a security vulnerability and the traditional approach to vulnerability management. In this blog, I will mainly spend time talking about the symptoms of vulnerability remediation, specifically in the context of Software Delivery/ Deployment. But in the interest of readers who don’t want to read my previous blog on Vulnerability Management, I will briefly cover the necessary concepts in this blog.
Understanding Vulnerability Remediation Process and Best Practices
Let me start off by briefly talking about “What is Vulnerability Remediation”, and “How Does Vulnerability Remediation Work?”.
What is Vulnerability Remediation?
Vulnerability remediation refers to the process of identifying and mitigating security vulnerabilities. These vulnerabilities could have arised either due to:
- Software errors
- Hardware issues
- Network misconfigurations
- Design flaws
- Human Errors
Remediating security vulnerabilities involves taking necessary actions, such as applying patches, making configuration changes, or implementing security measures, to eliminate or reduce the risk posed by vulnerabilities.
How Does Vulnerability Remediation Work?
The goal of vulnerability remediation is to enhance the security posture, protect sensitive data, and minimize the potential for cyberattacks or unauthorized access. The system’s security weakness can be addressed by following a simple 4-step process commonly adopted in the industry.
4-step process to Managing Vulnerabilities in production
Managing vulnerabilities and mitigating them swiftly can be achieved as part of a 4-step process:
- Detect: Detecting vulnerabilities through scanning and testing
- Prioritize: Understanding which vulnerabilities pose a real and significant risk
- Remediate: Patching, blocking, or remediating in real-time
- Monitor: Real-time alerts and notifications for newly discovered vulnerabilities
To read about this topic in detail, you can refer to my previous blog on vulnerability management where I have covered the importance of vulnerability remediation and how it works?
Shortcomings of Vulnerability Remediation in Software Delivery/ Deployment
The good news is that we’ve understood how to effectively trace and manage vulnerabilities. But that’s only half the story. The bad news is that this makes software delivery/ deployment even more difficult. Just because we know the different vulnerabilities that exist doesn’t mean we can adopt a rip-and-replace attitude while addressing the vulnerable code.
Here are some of the software delivery challenges as and when a vulnerability is reported:
- Ever changing Vulnerability landscape
- Inability to handle Zero-day exploits
- Auditing the software bill of materials during deployment
- Handling/ Documenting exceptions
Now, let me address these challenges in more detail.
1. Ever changing Vulnerability landscape
The biggest challenge with code deployment is the code itself. Even though no known vulnerability existed with a package/ dependency during code build, there is no guarantee that the same code will be non-exploitable during the time of deployment. If a vulnerability is reported between the time of code check-in and actual code deployment to prod/ test/ staging environments, you are still deploying code with vulnerable packages/ dependencies, leaving your environment vulnerable to an attack.
2. Inability to handle Zero-day exploits
While you still get notified of Zero-day vulnerabilities by some good-samaritans in the industry, you will still struggle to identify all the places in which a compromised package/ dependency is used in your code. This is primarily because you have to analyze a million lines of code and carefully identify if the vulnerability with a given CVE ID or package name is used or not.
3. Auditing the software bill of materials during deployment
Many times you may have been careful enough to avoid using vulnerable code in your deployment, but what’s the proof for it? Security Auditors would still need to run the necessary checks and sign-off for approvals before that code gets deployed.
4. Handling/ Documenting exceptions
In accordance to the previous point, a lot of the vulnerabilities would not really affect your systems due to the way you deploy it. But how do you document that, and create exceptions? The documentation is still a manual process, and will have to be manually remembered for as long as that exception remains in your code. And it is still a point of concern if the way that vulnerability is deployed in your environment changes.
How can OpsMx help address these challenges with Vulnerability management?
While it may be daunting to even just think of addressing vulnerable packages/ dependencies after reading the previous section above, I can rest assure you that OpsMx has certain capabilities that will make vulnerability tracing & mitigation in production a breeze.
Well the better news is, OpsMx’s Secure Software Delivery (SSD) capability combines the best of both worlds, i.e Security and Software Delivery. Our unique approach to software delivery/ deployment ensures that:
- Only secure code gets deployed into any environment (prod/ test/ staging)
- Any zero-day vulnerability that gets reported is automatically flagged by OpsMx SSD
- Any vulnerable package/ dependency in your code is automatically blocked from getting deployed during realtime
- Your code/ system is always in compliance with organization or industry-wide policies
- You have audit-ready reports to confidently display your security posture
Enough with the talk, and let me exactly drill down into how OpsMx’s SSD offerings addresses the challenges in the previous section.
Benefits of Vulnerability Tracing & Management with OpsMx SSD
- Post-code Pre-deployment checks
- Post-deployment checks to mitigate zero-day exploits
- Audit & Accountability system with D-BOM
- Effective Exception handling
Let me now explain the benefits in detail.
1. Post-code Pre-deployment checks
Every time any piece of code gets deployed, OpsMx’s Deployment Firewall checks the list of packages and dependencies against any open vulnerability. Even if the vulnerabilities get reported much after the code check-in by the developers, those vulnerabilities will get caught by OpsMx’s Deployment Firewall checks during the time of code deployment.
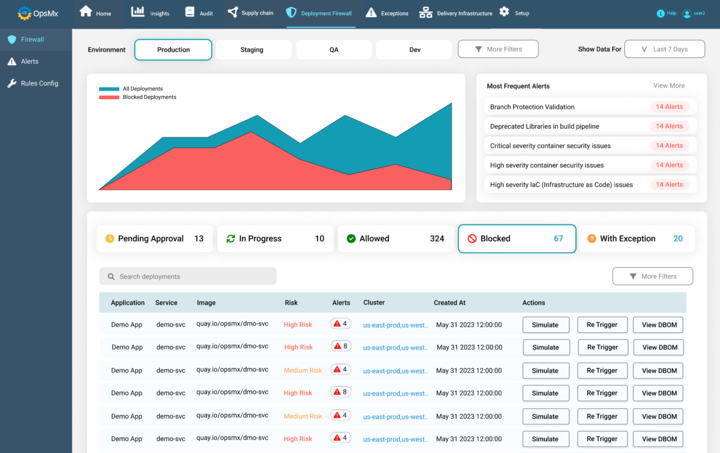
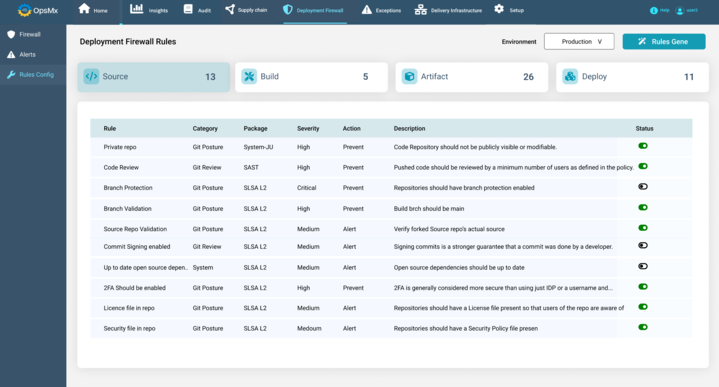
For ex: Consider the case that if the code is deployed 1 month after it is initially checked-in by the developer, and the vulnerability is reported sometime in between this time frame. In this case, the developer may have checked-in the code, but before it gets deployed, OpsMx will detect the compromised packages and block the deployment.
2. Post-deployment checks to mitigate zero-day exploits
Mitigating zero-day vulnerabilities is really the toughest challenge for security and development teams because it gets tedious to manually scan through the entire codebase and locate where the compromised package/ dependency is present. OpsMx’s SSD is like a deployment data warehouse of sorts, meaning it keeps track of every single package and the version number with any piece of code gets checked-in for deployment.
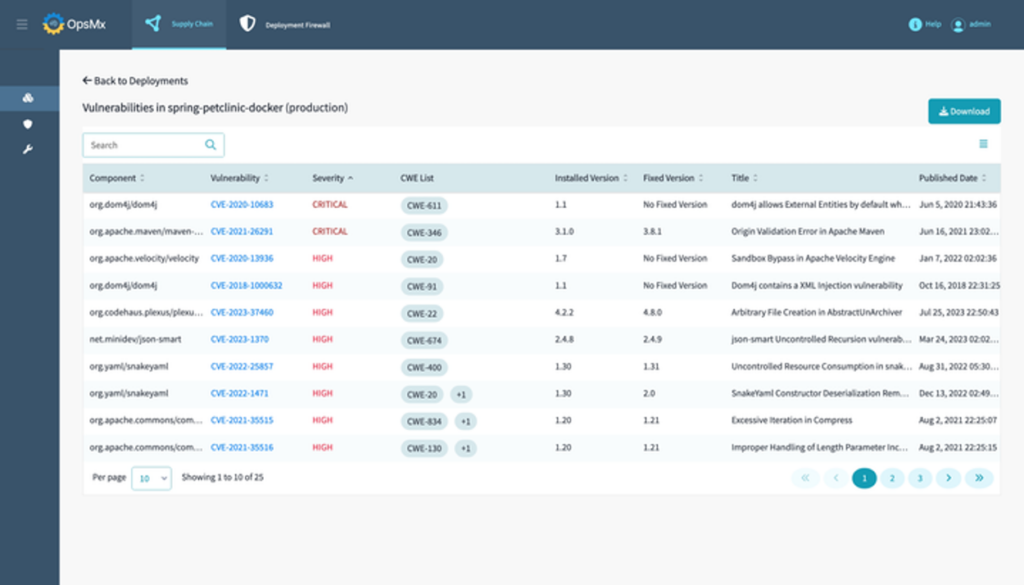
Instead with OpsMx, you can simply enter the CVE ID or the version number or the package name and OpsMx’s SSD will highlight all parts of the codebase where the compromised package is used and in which parts the code is vulnerable.
Infact, OpsMx’s SSD goes a step further by continuously monitoring deployed artifacts/ software and automatically alerts the user when a new CVE is detected or when a vulnerability is reported. As end users, you wouldn’t even have to scan or search for a CVE, our SSD will automatically send a Slack/ Email alert to the concerned user(s).
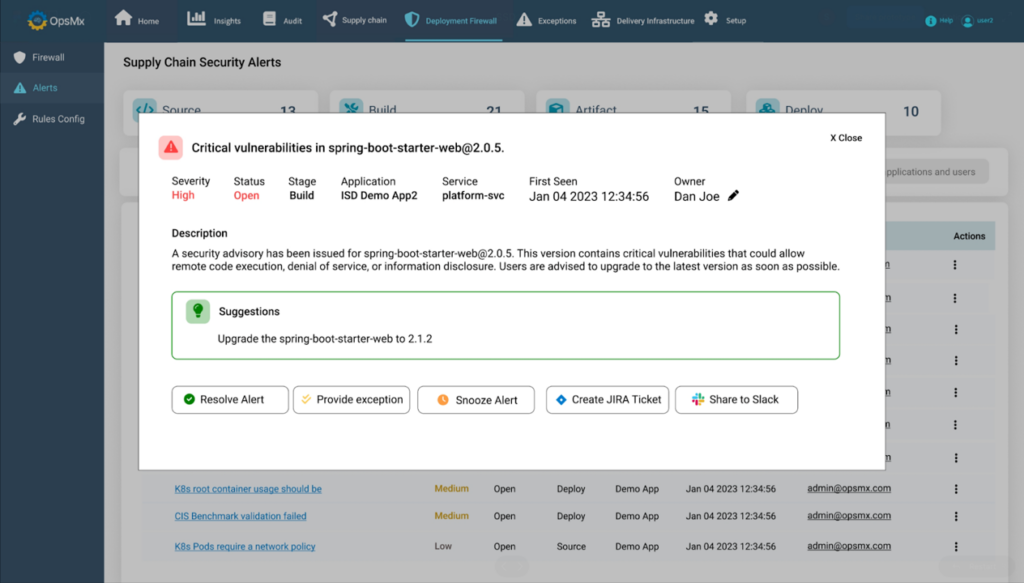
3. Audit & Accountability system with D-BOM
Surely a lot of care has been taken by your developers in using only the safe and secure packages/ dependencies in the codebase. But what’s the guarantee for that when auditors come asking around for compliance?
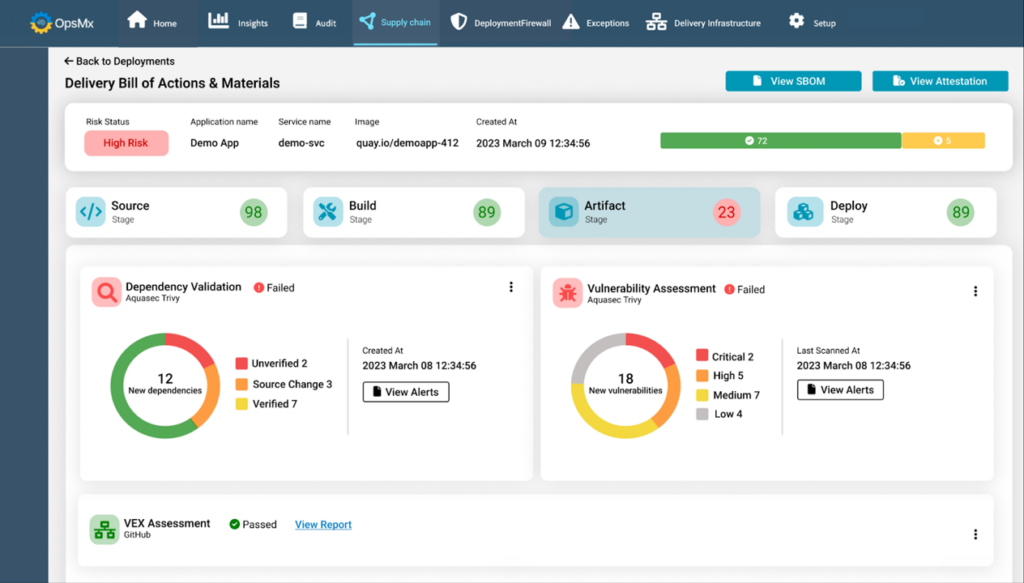
OpsMx’s Delivery Bill of Materials (D-BOM) acts like a pseudo Software Bill of Materials (S-BOM) where every single software package is tracked and maintained. The D-BOM can produce audit-ready reports that not only showcase compliance with industry and organization policies, but those that also confirm their overall security posture.
4. Effective Exception handling
Not all vulnerabilities are severe and exceptions can be made for some of them which won’t get exploited because of the way in which they are deployed. But the challenge lies in documenting the exception and time-boxing it so that it can be addressed at a later point in time.
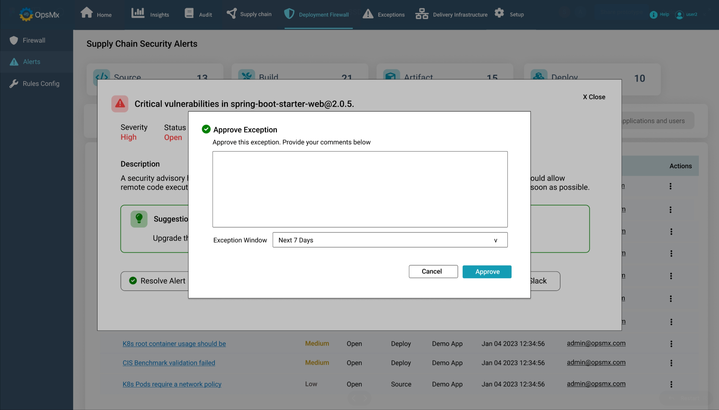
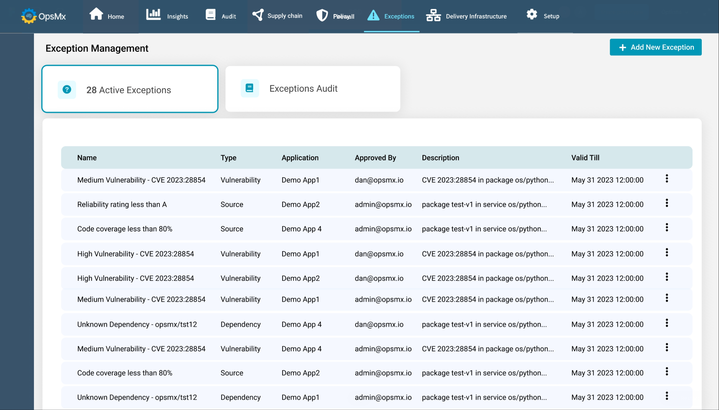
OpsMx’s SSD lets you do just that. You can quite easily document exceptions with all the necessary notes, and then time-box the exception to address it later.
I hope this blog helped you understand the importance of Vulnerability remediation and the need to develop a robust vulnerability remediation plan. Having such a remediation policy in place will not just give you a sense of direction on how to prioritize vulnerabilities, but it will also help you effectively manage them while provisioning software delivery/ deployment.
Conclusion
OpsMx’s Secure Software Delivery (SSD) comes packed with capabilities that bring together the best of two worlds – Security & Software Delivery. If you’re curious to know more about the offering, talk to our experts.





0 Comments