DevSecOps has ushered in a new era of secure software delivery, thanks to its proactive “Shift Left” strategy. This method, which advocates for the early and consistent inclusion of security measures, has revolutionized how we protect the integrity and safety of our software systems. Yet, our work is far from over! Post-build vulnerabilities can still sneak in, posing a threat to security. In this blog, we delve into five practical, automation-driven strategies to bolster software delivery security and dramatically cut down risk. Don’t let your organization be the next casualty of a security breach. Take action with these steps today.
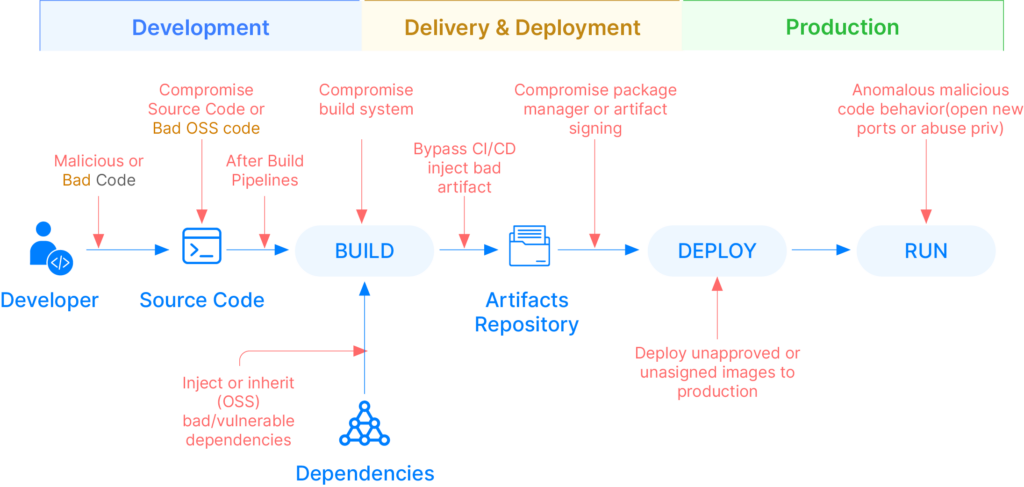
The Vulnerable Post-Build Stage
The post-build stage is crucial and vulnerable in software delivery. It’s where software artifacts take shape and are a breeding ground for security risks. Vulnerabilities, insecure dependencies, and unauthorized access can all seep in during this phase, putting your applications at risk. Addressing security issues at this stage is imperative to ensure your applications’ integrity and safety before they go live.
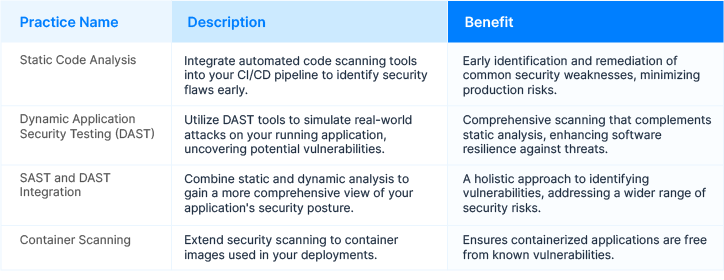
Step 1: Automated Security Scanning
Automating security scanning is your frontline defense. You can spot security flaws early by integrating automated code scanning tools into your CI/CD pipeline. These tools analyze your codebase, dependencies, and configurations to detect common security weaknesses like injection attacks, XSS, and authentication bypasses. Identifying vulnerabilities early empowers your team to take swift action and remediate issues before they escalate into production problems.
Best Practices for Automated Security Scanning:
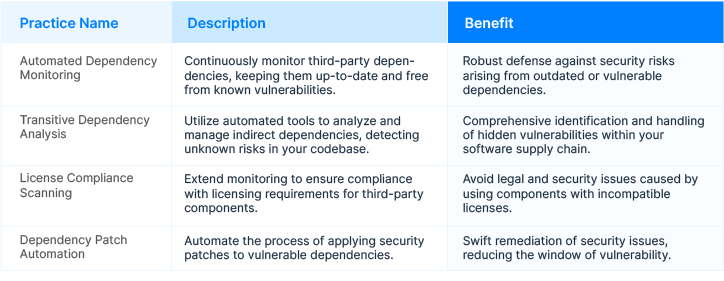
Step 2: Vigilant Dependency Management
Secure software delivery hinges on effectively managing third-party dependencies. Establish and enforce policies for handling vulnerable dependencies during the post-build phase. Automated tools continuously monitor these dependencies, keeping them up-to-date and free from known vulnerabilities. Regular scanning and updates reinforce your application’s defenses and minimize potential risks.
Best Practices for Vigilant Dependency Management:
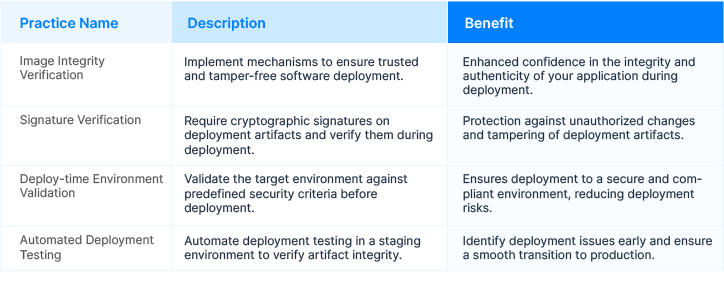
Step 3: Secure Deployment Verification
In the post-build phase, verifying the integrity and authenticity of your deployment artifacts is critical. Implement mechanisms that ensure only trusted and tamper-free software reaches your production environment. Image integrity and signature verification are powerful techniques to confirm the safety of your deployment artifacts. This step ensures your application is deployed with utmost confidence.
Best Practices for Secure Deployment Verification:
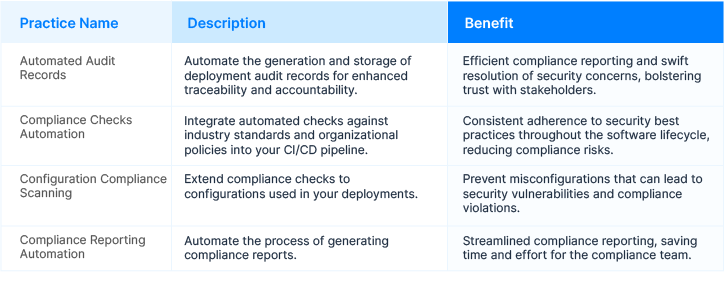
Step 4: Continuous Auditing and Compliance
Automate the generation and storage of deployment audit records during the post-build phase. Enhanced traceability and accountability are vital to demonstrating compliance with regulations and promptly addressing security concerns. An automated auditing process ensures you can respond efficiently to compliance requests, maintaining a secure software delivery pipeline.
Best Practices for Continuous Auditing and Compliance:
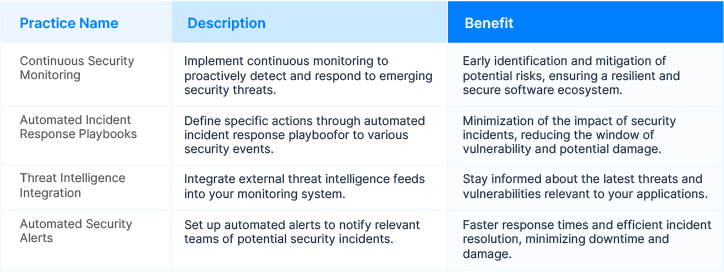
Step 5: Real-Time Monitoring and Incident Response
Continuous monitoring and security assessments post-build provide real-time risk visibility. This proactive approach keeps you ahead of emerging threats and potential risks. Early detection and rapincident responsents are paramount to maintaining a resilient and secure software ecosystem. Real-time monitoring allows you to act swiftly and mitigate potential risks before they escalate.
Best Practices for Real-Time Monitoring and Incident Response:
Conclusion
So, there you have it. These five actionable steps powered by automation will strengthen software delivery security and significantly reduce risk exposure. If you’re serious about securing your software delivery pipeline to download our eBook, “A Guide to Secure Software Delivery.” This eBook will give you everything you need to know to get started, including:
- A comprehensive overview of the security challenges facing software delivery teams today
- A step-by-step guide to implementing the five actionable steps outlined in this blog post
- Real-world case studies from organizations that have successfully implemented these steps
Don’t wait any longer. Download your copy of “A Guide to Secure Software Delivery” today and start securing your software delivery pipeline.
About OpsMx
Founded with the vision of “delivering software without human intervention,” OpsMx enables customers to transform and automate their software delivery processes. OpsMx builds on open-source Spinnaker and Argo with services and software that helps DevOps teams SHIP BETTER SOFTWARE FASTER.



0 Comments