Introduction
Security Assertion Markup Language (SAML) is a standard used for user login to different applications like Spinnaker, based on their logged-in sessions used in another context. This single sign-on (SSO) login standard has significant advantages over logging in using a username/password:
- No need to type in credentials
- No need to remember and renew passwords
- No weak passwords
The scope of this guide is how to set up SAML authentication on Spinnaker using Okta as the Identity Provider.
Pre-Requisites
- Desired version of the Spinnaker installed
- Okta account with required users
- Admin Access to the Okta to add the Spinnaker application
Setting up Okta Account
- Navigate to https://www.okta.com/
- Click Signup and register for a new account.
- Get your Okta Account URL.
Ex: https://opsmx-dev-admin.okta.com/
Configuring Spinnaker Authentication using SAML with Okta as IDP
- Configure a Spinnaker application in the Okta.
- Configure Halyard with Okta application.
A. Configure a Spinnaker application in the Okta
- Login to Okta as the administrator (https://opsmx-dev-admin.okta.com/) using administrator Login.
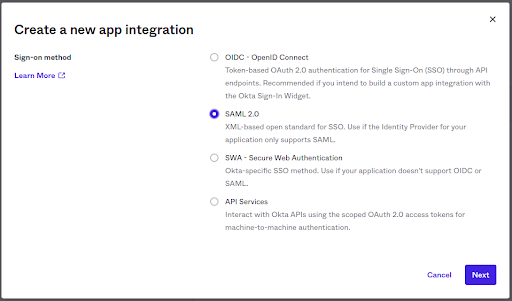
- Configure Spinnaker as a new SSO Application. ( Navigate to Applications —>Create App Integration —> SAML2.0)
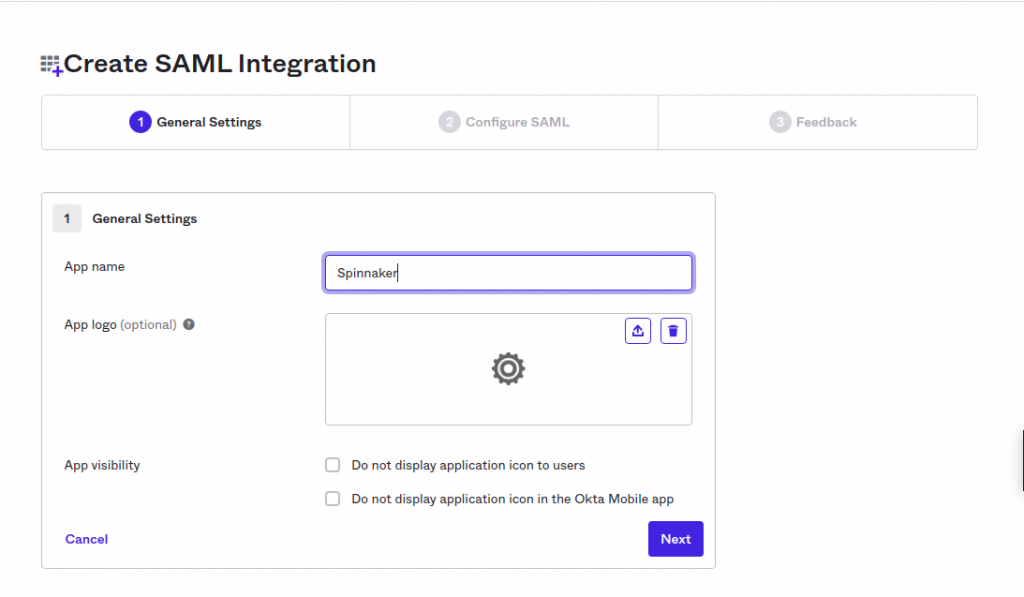
3. Provide the Required Name (e.g: Spinnaker) and Logo for the Custom Application.
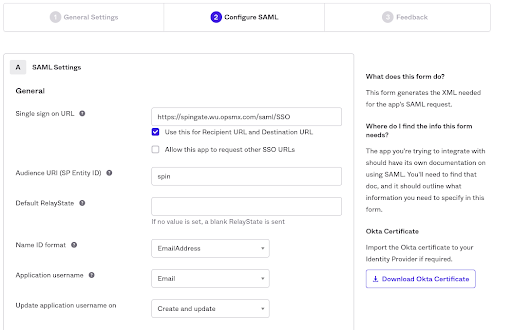
4. Provide the SAML Settings Configuration.
- Single sign-on URL: This is the EndPoint to which Okta will send the SAML responses. For Spinnaker it is basically the Gate URL + /saml/SSO.
- Ex: https://test-spin.opsmx.com/gate/saml/SSO
- Note: The End point URL should be followed by /saml/SSO.
- Audience URI (SP Entity ID): Entity ID here should match with the Issuer ID in Spinnaker Halyard
- Ex: spind
- Name ID Format : Identifies the SAML processing rules and constraints for the assertion’s subject statement. Use the default value of ‘Unspecified’ unless the application explicitly requires a specific format. Set this to EmailAddress.
- Application username: Determines the default value for a user’s application username. The application username will be used for the assertion’s subject statement. Set this to: Email.
- Group Attribute Statements:
- Name = memberOf, Name format = Unspecified, Filter = Regex: .*
- Click “Next”.
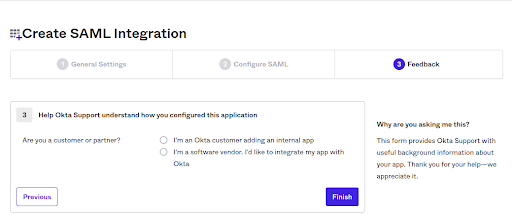
g. The Create SAML Integration Feedback page, select the “I’m an Okta customer adding an internal app” button, then hit the green “Finish” button.
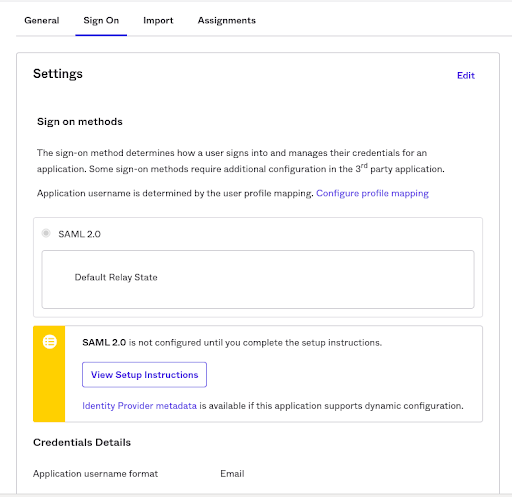
h. Navigate back to this page by going to Applications -> applicationName -> Sign On tab. Click the button “View Setup Instructions”.This will display the page with configuration information necessary to configure Spinnaker.
i. Download the Certificate and Save the metadata.xml file to your local. These are required to configure the Spinnaker.
J. Download the Certificate and Save the metadata.xml file to your local. These are required to configure the Spinnaker.
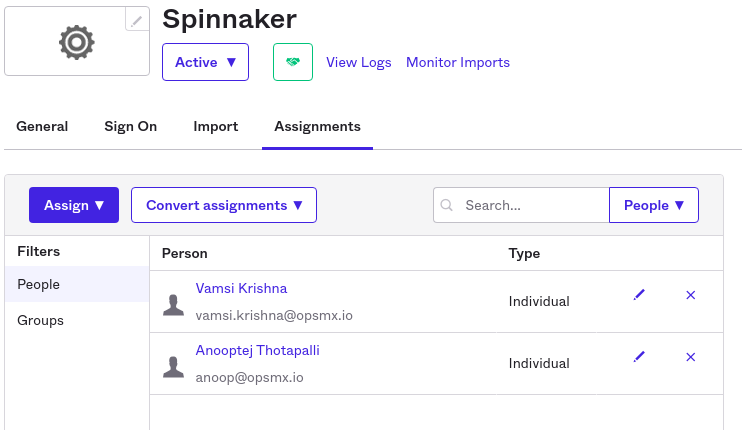
Finally, you can assign the required Users/Groups to access the Spinnaker Application.
B. Configure the Halyard to use the Spinnaker Okta for Authentication.
1. Create a SAML KeyStore for Spinnaker
keytool -genkey -v -keystore spinnaker.jks -alias saml -keyalg RSA -keysize 2048 -validity 10000
2. Configure the Spinnaker to use the Okta as SAML Authentication.
hal config security authn saml edit \
--keystore $KEYSTORE_PATH \
--keystore-alias saml \
--keystore-password $KEYSTORE_PASSWORD \
--metadata $METADATA_PATH \
--issuer-id $ISSUER_ID \
--service-address-url $SERVICE_ADDR_URL
SERVICE_ADDR_URL is the Spinnaker gate endpoint URL.
3. Enable SAML authentication.
hal config security authn saml enable
4.Apply the halyard changes
hal deploy apply
- 5. Verify Spinnaker authentication
Once changes are applied, you can verify Spinnaker authentication. It should take you to the Okta login page and should be able to authenticate to Spinnaker successfully.
About OpsMx
Founded with the vision of “delivering software without human intervention,” OpsMx enables customers to transform and automate their software delivery processes. OpsMx builds on open-source Spinnaker and Argo with services and software that helps DevOps teams SHIP BETTER SOFTWARE FASTER.


0 Comments