Thus far in 2023, ‘Security’ has been the theme surrounding any/ all emerging trends in Software Delivery. Be it the emergence of DevSecOps, or ‘Shifting-security to the left’, or ‘software supply chain security’, all of these trends are focussed on ensuring security is not an afterthought in software delivery/ deployment.
And rightly so, the astronomical increase in the number of security attacks on organizations in recent months is primarily due to their vulnerable software supply chain. And the supply chain becomes vulnerable when either the right security tools are not integrated into the delivery pipeline or when secure CI/CD tools lack even the basic security capabilities.
So in this blog, I explain why ‘Security capabilities’ must not just be an afterthought while evaluating CI/CD tools, but rather a primary consideration.
Why prioritize ‘Security’ when evaluating CI/CD tools?
While the use of security scanning tools can mitigate threats at the code level, we still don’t have a solution to curtail threats arising during software delivery. This is due to a variety of reasons, but very much related to the security posture in your CI/CD toolchain or a lack thereof.
How are CI/CD Tools and CI/CD Pipelines prone to Security threats?
Now let me explain how threat actors can leverage CI/CD tools as the attack vector.
1. Insecure Coding practices
Code that was free of vulnerabilities during code check-in, could end up reporting CVEs (common vulnerabilities and exposures) by the time of code commit. Vulnerabilities get reported all the time, and if the time delta between code check-in and code commit is long enough, then any vulnerability reported between code check-in and code commit will get deployed to prod (or any other environment) undetected. This will expose the CI/CD pipeline, with the CI/CD tool being the attack vector for threat actors.
2. Vulnerable/ Compromised 3rd Party packages
Another way in which vulnerabilities bypass CI/CD tools is during the ‘build phase’ in CI. If the CI tool builds a piece of code containing compromised packages or dependencies, then the compromised code will get deployed unless an external security scanning tool reports the vulnerability. So unless the CI/CD tool has an integration with external security tools, it will end up becoming another attack vector for threat actors.
3. Exposure of Secrets
Tools and resources within the CI/CD pipeline may at times require access to confidential information such as passwords, secrets key and API keys to communicate with each other or to perform complex actions. If these secrets are exposed in the CI/CD pipeline or DevOps environments, then they may allow an attacker to steal data, access corporate systems, or add malicious functionality to applications.
These are just a few scenarios how attackers can target CI/CD tools and pipelines. In the next section of this blog, let me talk about the impact of insecure CI/CD tooling on organizations and businesses alike.
Impact of not Securing CI/CD Tools and CI/CD Pipeline
By not giving security the due diligence it deserves, organizations risk tarnishing their value and brand image. Let me talk about this in further detail by reasoning out issues they will be faced with.
1. Inability to cope with future threats (evolving threat landscape)
Remediating serious security breaches is like climbing out of a slippery slope. If you’ve ever been on such a team you will know how difficult it is to not only remediate the existing issue, but also to prevent any further issues. Fixing security breaches often feel like getting caught in a never-ending spiral. By the time you arrive with patches to fix the issue, you are thrown onto a web of a dozen more issues.
2. Legal & Financial implications of hosting insecure application
Many industries today operate under strict regulations and guidelines. In highly regulated industries like Banking and Healthcare, organizations must adhere to standards established by the governing body and comply with certifications such as HIPAA and HITRUST. Within the software industry, FEDRamp is a compliance certifications that needs to be complied with for any Cloud Service Providers (CSPs) wishing to provide Cloud Service Offerings (CSOs) to the US government. SOC, ISO/IEC 27001, and GDPR are other famous certifications. If any organization is found to be in non-compliance with standards established by such governing bodies, either the company’s license to operate is ceased, or they are allowed to continue operations only after settling heavy fines and dues.
3. Reputational damage as a result of vulnerabilities and exposures
Most organizations that suffer security breaches take measures to recover and improve their security posture. However, there have been instances where security breaches have had such severe consequences that they contributed to the demise of the business or severely impacted their ability to recover in the eyes of the customer. Myspace is a fine example of a pioneering social networking giant that never quite recovered after a serious breach on their network. Other such examples include Yahoo and Equifax.
Takeaway
As of 2023, prioritizing security when evaluating CI/CD tools is not just a best practice; it is a necessity to protect your organization from evolving threats, legal implications, and reputational damage. Security should be a fundamental consideration throughout your software development and deployment lifecycle.
How can you prioritize ‘Security’ in CI/CD Pipeline?
Prioritizing security should be a conscious decision, with full backing from stakeholders and business leaders within the organization. The solution is to either incorporate more security tools within your CI/CD pipeline or, to make sure your existing CI/CD tooling is equipped with the relevant security capabilities.
This is where OpsMx adds a ton of value. OpsMx SSD (Secure Software Delivery) is a Security-focussed Continuous Delivery tool that can help you achieve DevSecOps and improve your overall security posture by providing security guardrails, establishing compliances & policies, and performing audits.
You can either use OpsMx directly as your delivery orchestration tool or integrate OpsMx’s DevSecOps capabilities with your existing CI/CD tooling. OpsMx SSD is platform agnostic and works with GitLab, GitHub, Argo, Jenkins, and Spinnaker.
Now let me go into further details and explain how any secure CI/CD tool (even if it’s not necessarily OpsMx) protects the CI/CD pipeline, and improves the security posture.
How OpsMx improves Security in your CI/CD pipeline
1. Securing the Software Supply Chain
With the increasing use of third-party libraries and dependencies, securing the software supply chain is critical. Secure CI/CD tools (such as OpsMx) can automatically scan dependencies for known vulnerabilities, ensuring that you are not introducing vulnerabilities through external code.
OpsMx SSD comes with an intelligent module called Deployment Firewall which checks the list of packages and dependencies against any open vulnerability. It doesn’t matter at what time the dependency gets introduced into the codebase, because during code deployment the Deployment Firewall will automatically scan all packages, libraries, & dependencies and block any or all reported vulnerabilities.
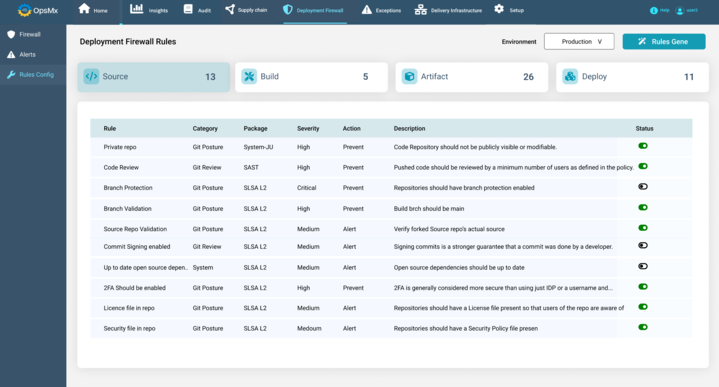
2. Data Protection and Compliance Management
Data protection regulations such as GDPR, CCPA, and HIPAA have stringent requirements for the handling of personal and sensitive data. Using insecure CI/CD tools can lead to data breaches, legal consequences, and fines. Security-focused CI/CD tools help you maintain compliance with these regulations.
OpsMx’s PolicyGenie/ RulesEngine can be used to define policies and ensure compliance as per organization/ industry regulations. Enforce security by defining rules on top of the incoming data from different DevOps tools. Thus, OpsMx’s compliance enforcing mechanism ensures that industry best practices and established regulatory mandates are followed.
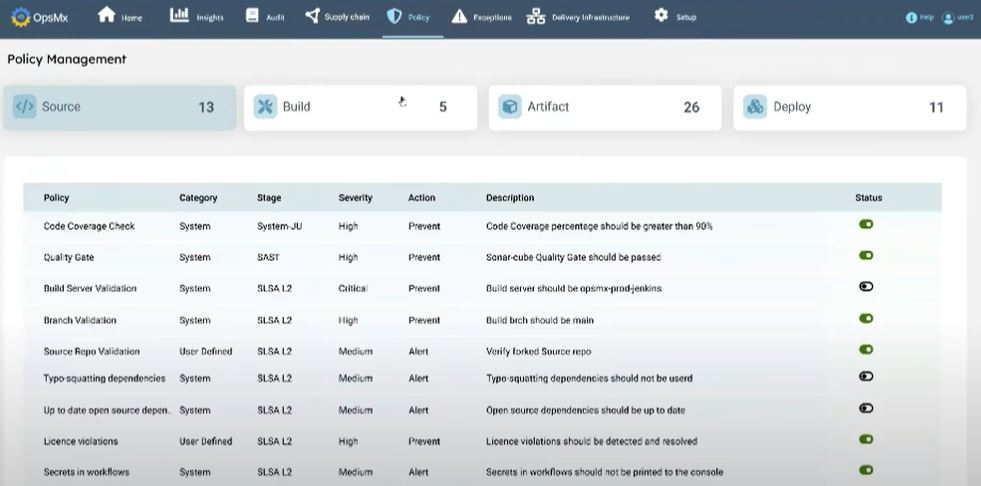
3.Code Integrity
Security vulnerabilities in code can have disastrous consequences, leading to data breaches, financial losses, and reputational damage. Secure CI/CD tools often include features like static code analysis and vulnerability scanning to identify and address security issues early in the development process.
When a secure CI/CD tool doesn’t natively support AppSec functionalities (as is the case with OpsMx) such as static code analysis and vulnerability scanning, there should be work around to achieve the same. In the case of OpsMx, we integrate with 70+ DevOps and Security tools. By integrating OpsMx and different tools for Application Security in your CI/CD pipeline, you can leverage scan results to automate the deployment approval process.

4. Real-time Vulnerability Tracing and Incident Response
Security is an ongoing process, and CI/CD tools should support continuous monitoring and incident response capabilities. This includes real-time alerting and the ability to roll back deployments quickly in case of a security breach.
Especially when it comes to mitigating zero-day exploits, OpsMx’s SSD has the capability to automatically detect newly reported vulnerabilities (such as the Log4j shell reported in late 2021) that may be present within your deployed codebase. OpsMx SSD continuously monitors your deployed artifacts/ packages and automatically alerts the user when a new CVE is detected or when a vulnerability is reported. As end users, you wouldn’t even have to scan or search for a CVE, our SSD will automatically send a Slack/ Email alert to the concerned user(s)
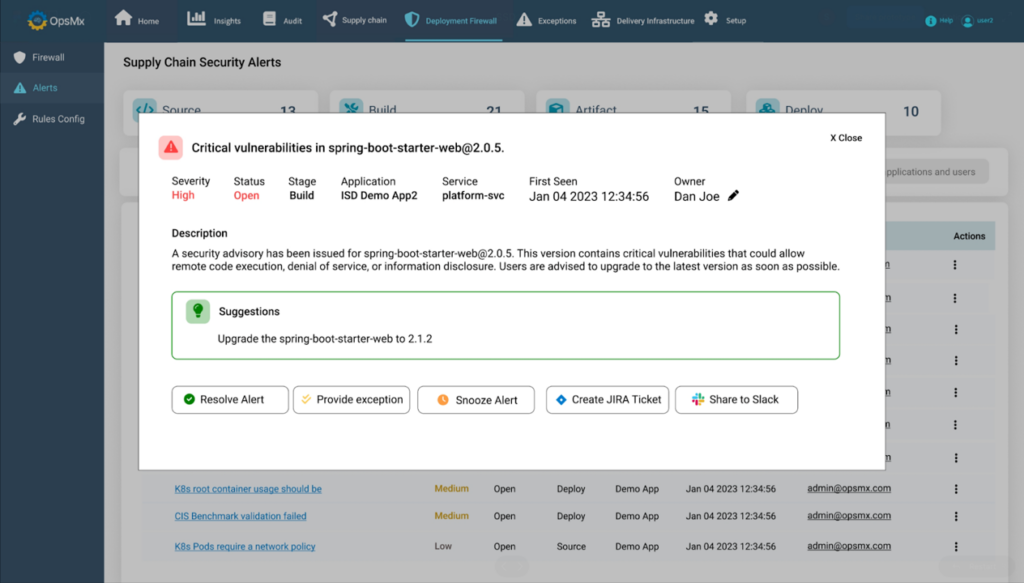
5. Secure Configuration Management
Misconfigured CI/CD pipelines can introduce security vulnerabilities. Security-focused tools provide best practices and templates for secure configuration management.
6. Securing Containerization and Orchestration
If you’re using containerization and orchestration tools like Docker and Kubernetes, security should be a top concern. Secure CI/CD tools integrate with these technologies to help you effectively manage container security.
OpsMx comes with a DevSecOps Control Plane that gives you a unified view of your deployment health. The centralized dashboard displays data by gathering, synthesizing, and correlating data from across the full set of DevOps and security tools. This unified and normalized view can help you understand the security posture of different applications in your deployment, collaborate with other users, teams, and take actions accordingly.
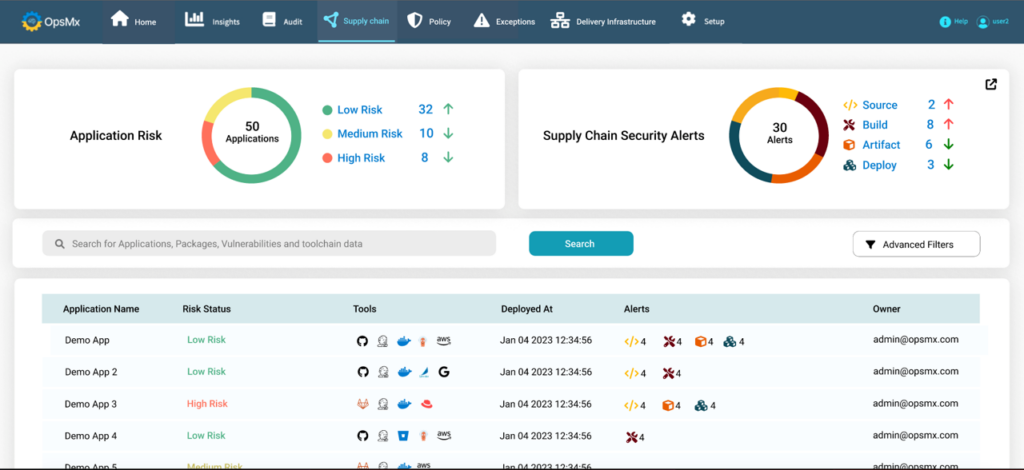
Conclusion
I hope this blog helped you understand the importance of using secure CI/CD tools within your deployment pipeline. If you are in the inception phase of setting up a CI/CD pipeline, then I highly recommend checking out OpsMx’s SCD (Secure Continuously Delivery) – which is a one stop solution to help you improve both, security as well as velocity during software delivery.
But if you’re merely looking to incorporate DevSecOps capabilities within your existing CI/CD toolchain, then I recommend you to check out OpsMx SSD (Secure Software Delivery). SSD improves security posture by giving you greater security insights, helping you define policies and manage compliances, and stay audit-ready for when inspectors from regulatory bodies come knocking at your door.



0 Comments